What Happens After BGP?
Gaining Full Path Visibility in Hybrid Cloud Networks In the modern enterprise, Border Gateway Protocol (BGP) plays a foundational role in connecting distributed networks. It is the routing protocol that...
When under attack from network security threats, you have any number of tools — intrusion detection systems (IDS), intrusion prevention systems (IPS), antivirus software, security information and event management (SIEM) technologies — that waste no time in sending you an alert that something is wrong.
When a potential threat is identified, speed is of the essence. The quicker network security threats can be located, isolated and mitigated, the less chance there is for actual damage or loss to occur. While the alert process is completely automated, which is why almost no time is wasted in detecting issues, the typical security-response workflow is still very much manual and time-consuming. This where visibility and automation come in.
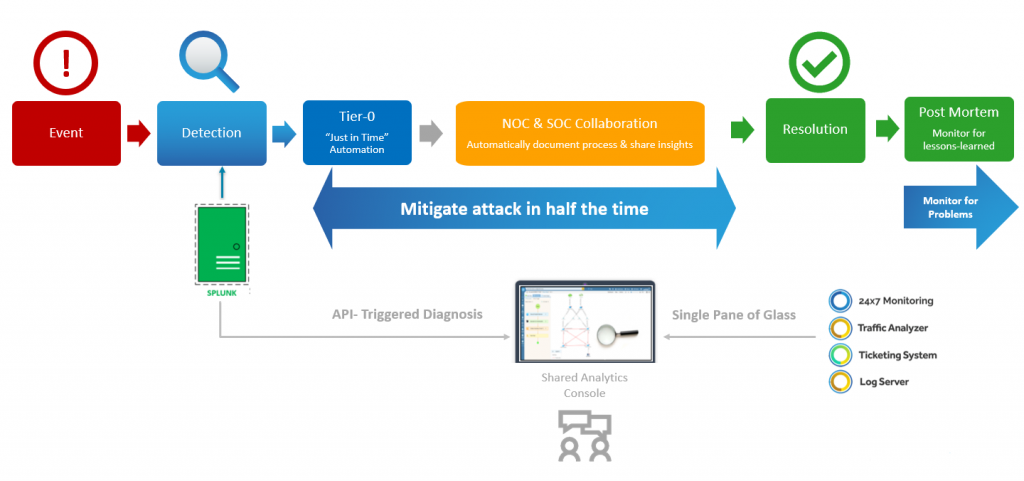 When every second counts, “just in time” automation triggers a tier-0 diagnosis that cuts attack-mitigation time dramatically.
When every second counts, “just in time” automation triggers a tier-0 diagnosis that cuts attack-mitigation time dramatically.
First and foremost, you have to understand the impact of network security threats. Your IDS/IPS or SIEM won’t provide you with much insight, other than letting you know there’s potentially malicious traffic. Your network diagrams give you a sense of how the network is connected, so you’ll see what the potential impact is. But diagrams are all too often incomplete or outdated. You either have to rely on your memory — which becomes increasingly challenging with complex, multi-vendor, software-defined and hybrid environments — or manually issue a bunch of CLI commands and pore through reams of text output. This gives you visibility into the configuration and design at the device level, but not the network level. That’s a lot of time to get a very limited view of the situation. And when all else fails, you’ll need to escalate things to a more senior level engineer. But as we all know, finding the expert who can stop the bleeding is easier said than done. Traditional “data silos” between the NOC and SOC make collaboration and escalation less than seamless — different teams rely on different tools and different systems and different data sets.
Let’s say that an attacker attempts to overwhelm a targeted device with ICMP echo-request packets (ping flood). Your IPS detects the threat and generates an SNMP trap to Splunk. Splunk receives the trap and, using a search-and-alert mechanism, triggers an API call to NetBrain with input parameters Source (attacker) and Destination (victim).
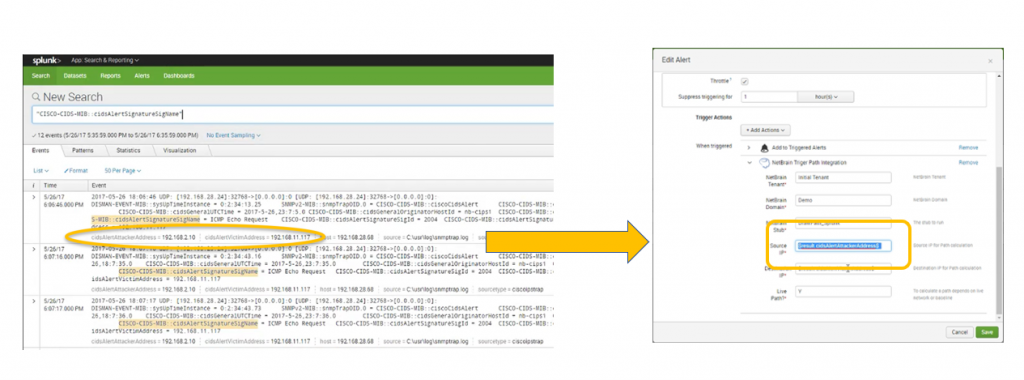 As soon as Splunk detects network security threats, API calls triggers NetBrain to automatically map the problem area are and diagnose the issue in real time.
As soon as Splunk detects network security threats, API calls triggers NetBrain to automatically map the problem area are and diagnose the issue in real time.
NetBrain then does two things automatically:
We call this a tier-0 diagnosis because all this triage and analysis happens automatically, before any human gets involved. The “just in time” automation capabilities give you real-time insight into and analytics about network security threats while they’re happening.
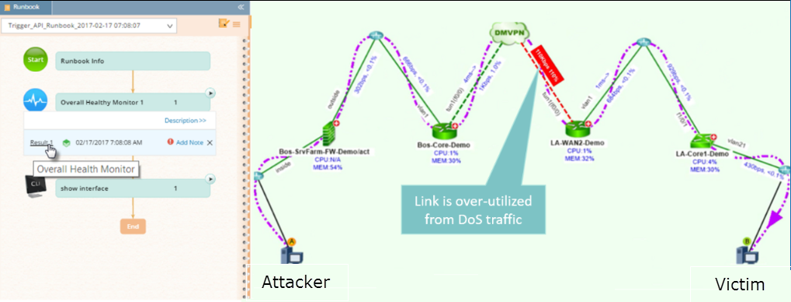
NetBrain automatically creates a Dynamic Map of the attack path, and Executable Runbooks automatically collect and analyze all the data for you.
All diagnostic results are recorded right inside the Runbook. This shared analytics console allows everybody to see who did what when — eliminating the need to reinvent the wheel during escalation (run same analyses that the previous engineers did) and getting different teams (NOC and SOC) on the same page to mitigate an attack. In fact, a NetBrain survey found that the lack of collaboration between network and security teams was the #1 challenge when troubleshooting network security issues. NOC and SOC teams can automatically document processes (by customizing Runbooks on the fly with whatever next best steps should be taken) and share critical insights that drastically reduce time to resolution.
For a long time, organizations have had the ability to automatically generate alerts when apparent network security threats attack their network. Isn’t it about time that the engineers charged with mitigating these attacks had the same level of automation in their arsenal?
Learn more on how NetBrain can assist you in your security efforts.
Check out our blog on Ensuring Effective Security and Network Collaboration.