DORA: What Financial IT Must Know
The Digital Operational Resilience Act (DORA) entered into application across the European Union on 17 January 2025, reshaping how financial institutions manage cyber and operational risk [1]. Although the United...
Network security remains a challenge for enterprises: a cat and mouse game of trying to keep up with the technical advances of well-funded cyber adversaries. Yet, sometimes it’s the simple things that make the biggest difference.
Effective collaboration can often represent the difference between a well-engineered, timely response to a threat and falling victim to a cyberattack. Our State of the Network Engineer 2017 survey reveals that the #1 challenge when troubleshooting network security issues is the lack of collaboration between network and security teams in mitigating an attack, selected by 72% of all respondents.
A recent article at Search Networking on the importance of collaboration got us thinking about how most organizations handle SecOps. It led to the fundamental question: What should security teams and network teams be doing to ensure they can collaborate in the moments that matter, when their network is at risk? We’ve outlined two key focus points to effective network and security collaboration tomorrow.
The simple reality is that identifying threats and troubleshooting attacks is primarily about visibility.
Democratizing Knowledge
Many organizations emphasize a commitment to collaboration, but without the right tools and processes in place, effective collaboration is difficult.
Enterprise networks are complex systems that are operated by teams, not individuals. They are often distributed geographically, with different technical skills and cultures. There is also crossover; for example, it is common for a network security engineer to operate on the network team and interact with an information security Officer within the security team.
The trap many enterprise organizations fall into is that critical network knowledge ends up residing with just one or two network experts. These experts have worked at the organization for years and know the ins and outs of the network better than anyone. But what happens when they aren’t there? Without these “tribal leaders,” network teams lack the knowledge to effectively troubleshoot or mitigate complex threats. Organizations which lack a culture of collaboration have pockets of knowledge solely stored inside the brains (or perhaps local hard drives) of tribal leaders. Many IT organizations fail to implement tools and practices which facilitate knowledge-sharing of this kind.
Streamline Data Sharing
Teams struggle to share data effectively – which is crucial at the task level, where insights and conclusions are made as a team. Teams traditionally communicate via web conference or email, where the sharing of data is clunky – usually in log files and data dumps. With these methods, it is challenging for one individual to draw insights from another individual’s data dump. By relying on manual methods of data collection and sharing (e.g. box-by-box, screen scraping or legacy home-grown scripts), teams are less effective.
With NetBrain, all relevant data is embedded within a Dynamic Network Map which can be easily shared as a link, circumventing outdated ways of sharing information. The result is quicker response times, faster threat mitigation, and improved collaboration.
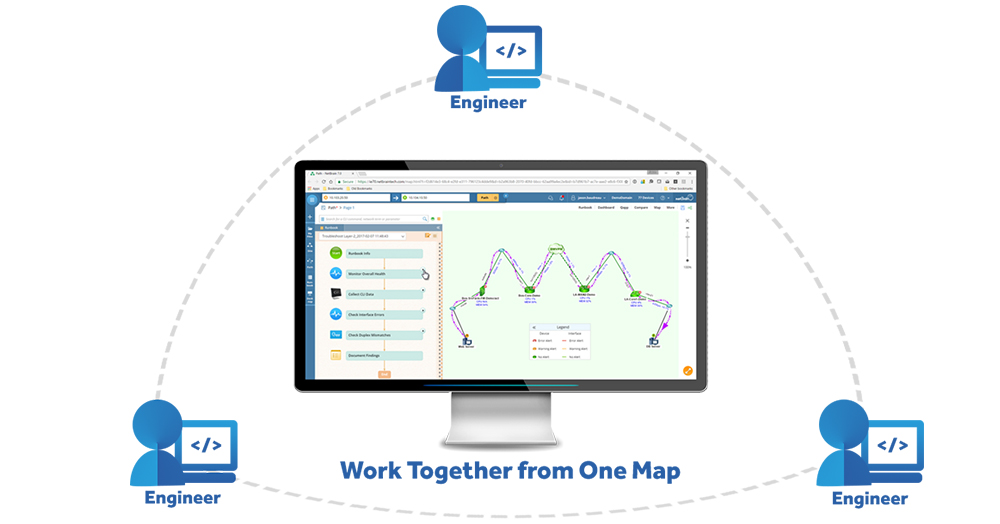
If You Can’t See, You Can’t Collaborate
Both these steps come back to the same basic idea – visibility is critical to collaboration. When every engineer has insight into relevant information and doesn’t have to rely on tribal leaders, security and network teams can collaborate more effectively.
The simple reality is that identifying threats and troubleshooting attacks is primarily about visibility. In most cases, the methods that network and security teams use to collect and analyze data are manual and labor intensive. The outputs of these traditional methods of network management often result in limited visibility or an overload of information that gives network engineers little actionable data.
With NetBrain at the center of the network and security management process, end-to-end visibility drives this collaboration.