The new European General Data Protection Regulation (GDPR) requires that your IT network meets strict standards for IT and data security. The regulations can be difficult to understand and ensuring GDPR compliance can be a nightmare if you’re tasked with managing a large enterprise network. Where do you begin?
It’s not enough to comply with GDPR – you have to prove it with documentation. And trying to document an enterprise network manually is playing with fire.
What is GDPR and how does it affect a network environment?
 Common questions related to GDPR compliance for IT infrastructure and data security teams include:
Common questions related to GDPR compliance for IT infrastructure and data security teams include:
- Which GDPR technology requirements are necessary?
- How can the transparency of the network and IT infrastructure be guaranteed?
- What documentation is required for GDPR compliance?
- How can sustained GDPR compliance with the statutory standards be ensured?
The General Data Protection Regulation (GDPR) (EU) 2016/679 is a new regulation on data protection and privacy for all individuals within the European Union as well as the export of sensitive data outside the EU. The GDPR compliance requirements begin on May 25, 2018.
The goal of the GDPR is to unify the statutory standards within the EU and increase data protection in the countries of the EU. EU citizens must give their express consent to the processing of their personal data. In addition, data subjects have the right to have this information deleted if it is no longer needed for the purpose for which it was collected, or if the consent is withdrawn. The type of data and the duration of time for which it is stored must be clearly understandable for individuals. Furthermore, companies that record and use personal data must be able to prove that they have consent for the data to be processed.
Among other things, companies must also report data breaches to the lead supervisory authorities within 72 hours.
It should also be noted that although the GDPR is a regulation for the countries of the EU, it also applies to all companies worldwide that offer goods or services in the EU as well as to those who have European employees and therefore record, process, and store the data of EU citizens.
Penalties for non-compliance with GDPR
“44 percent of companies surveyed are not yet sufficiently prepared for the GDPR and have taken no specific technological or organizational measures to prepare for it.”
– IDC Research
The new GDPR regulations have substantial effects on how your company manages data in a network environment. Penalties for non-compliance are very stiff – fines of up to four percent of the company’s annual turnover or up to 20 million euros – in addition to the affected person’s right to damage compensation.
To avoid these penalties, you’ll need to be able to ensure that your network is compliant – and be able to prove it.
GDPR and IT Security
The GDPR ascribes very high importance to IT security. One of the most important regulations in the GDPR in this regard is Article 32. This article describes which criteria are to be applied to organizational and technical measures in order to achieve a suitable level of GDPR network security:
With due regard to the state of the art, the costs of implementation and the type, scope, context and purposes of processing, as well as the varying probability of occurrence and severity of the risk to the rights and freedoms of natural persons, the controller and the processor shall take suitable technical and organizational measures to ensure a level of protection that is appropriate to the risk; these measures include, but are not limited to, the following:
- The pseudonymization, data minimization, and encryption of personal data
- The long-term ability to ensure the confidentiality, integrity, availability and resilience of systems and services in the context of processing
- The ability to quickly recover the availability of the personal data and access to it in the event of a physical or technical incident
- A procedure for regularly testing, assessing and evaluating the effectiveness of the technical and organizational measures for ensuring the security of processing
In particular, the risks that are associated with data processing – especially through destruction, loss or modification, whether unintentional or unlawful, or unauthorized disclosure of and/or unauthorized access to, personal data that was transmitted, stored or otherwise processed – must be considered when the appropriate level of protection is assessed.
Six Steps to Ensure GDPR Compliance
If you’re just getting started planning GDPR compliance for your IT infrastructure, it can be hard to know where to begin.
Network automation is an important part of a GDPR implementation plan that can help you simplify the planning and implementing of GDPR in a network environment — as well as to help you prove ongoing GDPR compliance. Network Automation can help you:
- Visualize and document your IT network
- Take appropriate measures and put automated processes in place for your network environment
- Ensure security and compliance with the statutory standards to avoid strict financial penalties
Below we outline the six most important steps to achieve GDPR compliance for your network — and discuss how network automation can ensure your organization stays in compliance.
STEP 1
Get a complete overview of your network
The first step to address GDPR compliance is to review a current, end-to-end overview of your network to understand the data streams which can contain security risks.
Comprehensive documentation is one of the most important steps needed to be able to prove compliance with GDPR statutory standards. But manual documentation of existing network infrastructure is time-consuming and costly, and this documentation is outdated almost as soon as it is completed.
Thanks to in-depth network discovery and Dynamic Maps, NetBrain allows you to get a comprehensive overview of your entire network infrastructure at any time on demand in seconds – even in multi-vendor and hybrid environments (physically/virtually/software-defined). It can even update automatically each time a network change occurs.
This allows you to ensure 100% accuracy of your network documentation — providing total transparency while saving time and money — to confidently address risks related to GDPR compliance requirements.
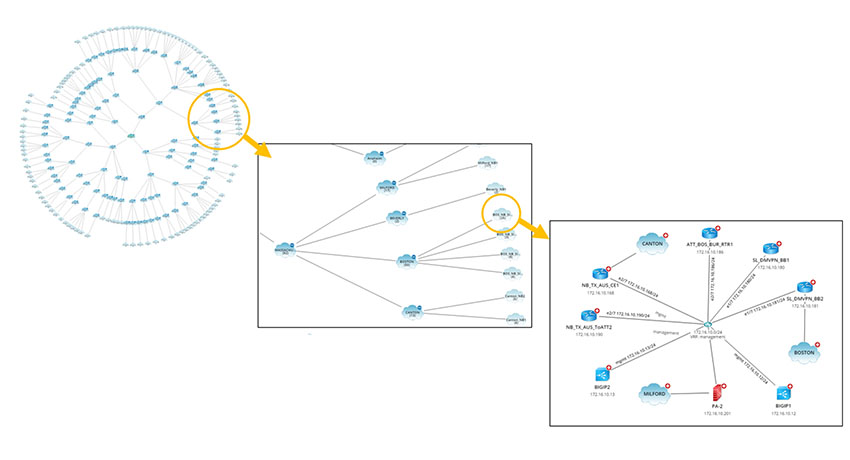
NetBrain’s Dynamic Mapping allows you to get a complete overview of your entire network infrastructure at any time on-demand in seconds to ensure you meet GDPR’s requirements for network documentation.
STEP 2
Use a comprehensive information display for your network
If information on your network infrastructure is distributed across different tools it is difficult to get insights to recognize, document, and immediately respond to network problems, attacks, security, and any data breach. This is very dangerous because the law requires you to maintain (and prove!) GDPR compliance across your entire network at any time.
NetBrain offers a RESTful API framework that integrates other network-management solutions such as monitoring, GDPR IT security, ticketing, and logging systems. Information from these tools can be visualized in a single location to be used for comprehensive analyses regardless of data source, quantity, or format.
For example, if an incident occurs in a ticketing or monitoring system, a NetBrain diagnosis can be initiated automatically so that the data can be visualized and immediately analyzed. IT staff can also incorporate security diagnoses (IDS/SIEM) via API in order to identify the affected network segment in the network map to depict the threat from an attack on the company network.
STEP 3
“60 percent of companies do not think that their data is sufficiently protected, and 63 percent must modernize their security architecture to comply with GDPR.”
– The Ponemon Institute
Identify and fix security vulnerabilities
NetBrain’s adaptive network automation examines each network configuration on the basis of a range of pre-defined GDPR compliance rules for each device:
- Are the device passwords encrypted?
- Are timeouts configured?
- Are the default settings of the supplier still being used?
If a device is not performing in compliance with the law, our software will alert you.
Fixing security vulnerabilities is also often still a manual — and very slow — process. NetBrain automates this process quickly and reliably. The required changes can be implemented in an ITIL-compliant manner with an additional change-management module.
STEP 4
Standardize your security processes
Implementing guidelines and defined security precautions can be a challenge.
Most companies make continuous changes to their networks but often do not document these changes sufficiently or do not observe the security guidelines in the process – and they diverge further and further from the statutory standards.
IT staff can prevent this by using executable runbooks from NetBrain to implement recurring tasks and rules and running these repeatedly at defined times. These Runbooks may also contain design guides and best practices in order to be able to carry through established procedures for a secure IT infrastructure and network operations.
For example, after a change in the network infrastructure, the administrators can execute a runbook to evaluate vulnerabilities to ensure that these correspond to the pre-defined security standards.
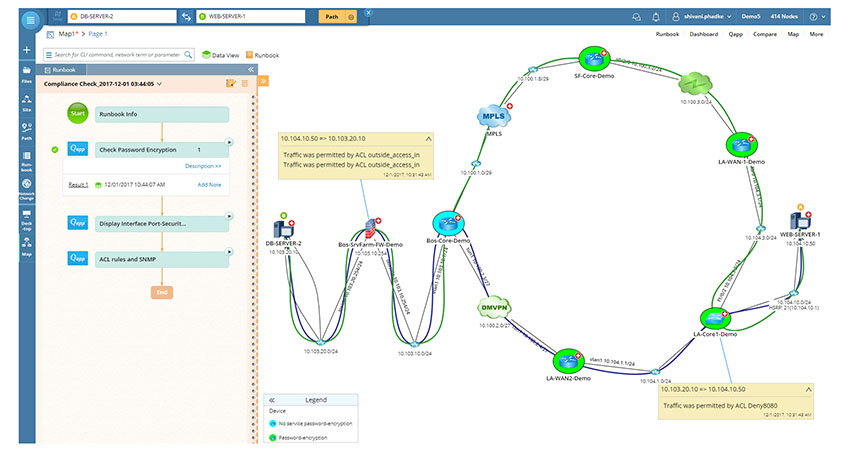
NetBrain’s executable runbooks automatically evaluate security vulnerabilities to ensure that your network complies with GDPR security requirements. These runbooks automatically alert you when there’s a problem so you can quickly take action.
STEP 5
Increase the degree of automation
In order for companies to be able to prove to a data protection officer that their infrastructure is secure and their data management practices comply with GDPR, they must use tools that require the least possible amount of manual operations and instead provide the desired information and documentation at the touch of a button.
Increasing the degree of automation for network analyses, data visualizations, diagnoses, and audit documentation will ensure that the results are more efficient, accurate, and consistent.
STEP 6
Ensure sustained GDPR compliance with the law
Modern IT infrastructures are no longer static — they often change continuously. This also applies to the threat situation.
In order to be able to ensure sustained GDPR compliance and guarantee IT security, companies must view compliance with standards as an ongoing process and not a one-time procedure. The cooperation of various teams (security, network, organization, etc.) is also necessary for these processes to run smoothly.
With NetBrain, these teams can collaborate on the same network plan during triage and forensics to prevent attacks. This ensures that the procedures for compliance with GDPR statutory standards are implemented consistently and that all IT teams follow the defined security practices in unison, even if they are distributed over various locations.
Partner with NetBrain
Implementing GDPR IT infrastructure while manually documenting your network can be frustrating. However, proper network automation and security controls can help you demonstrate compliance with less effort. With a partner, GDPR compliance in IT becomes an even smoother process.
At NetBrain, we demonstrate how to implement GDPR compliance by taking you through the six processes of ensuring your network is compliant. We help you document and visualize your IT network without worrying about non-compliance with GDPR IT requirements.
Through networking mapping, we allow you to have real visibility of your entire network environment to help you understand your network structure. We also ensure your documentation is 100% accurate by providing automatic updates each time there’s a network change. Updates ensure your IT and GDPR compliance is current.
Get our network visualization tools to improve network management, help you react to network issues, and safeguard personal data. Backed by a robust customer success program, we continually innovate to help our customers transform their networks in a complex multi-cloud world.

 Common questions related to GDPR compliance for IT infrastructure and data security teams include:
Common questions related to GDPR compliance for IT infrastructure and data security teams include:
