What Happens After BGP?
Gaining Full Path Visibility in Hybrid Cloud Networks In the modern enterprise, Border Gateway Protocol (BGP) plays a foundational role in connecting distributed networks. It is the routing protocol that...
It’s Monday morning and your network is down. You had a PCI compliance audit coming up, so over the weekend you locked down some firewall rules and made some ACL changes. Clearly, those changes didn’t have the effect you intended. Your network monitoring system has caught the problem — after the fact, once business has been disrupted. Wouldn’t it have been great to see the impact of those changes beforehand?
In the age of large and ever-changing networks, proactive beats reactive every time. Most network monitoring can offer only retroactive alerts that something has already gone wrong. The better monitoring solutions may even guess at what and where the source of the problem is. But that’s not quite enough anymore, not when every minute of downtime costs tens of thousands of dollars in lost revenue. The time for network verification is now.
Network World recently wrote about the many ways in which network verification is more powerful than monitoring. Network monitoring tools can understand the impact of network changes only after users have already experienced the result. Network verification, however, takes it a step further to thoroughly analyze how network traffic actually flows after making changes without needing users as “live ammo” and whether that flow matches the desired paths. This more accurate view of traffic flows allows network engineers to determine definitely and proactively whether their changes had the intended effect (or not).
In networking, engineers must be able to ensure that traffic is flowing as the design intends. For example, the network design may intend for traffic to be permitted between point A and point B:
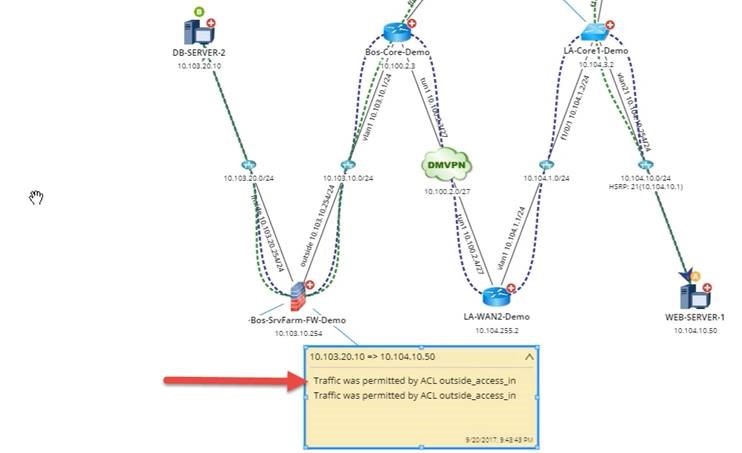
But it may also intend for traffic to be segmented between point A and point C, say, for security purposes because credit card data is involved and therefore needs the added layer of security.
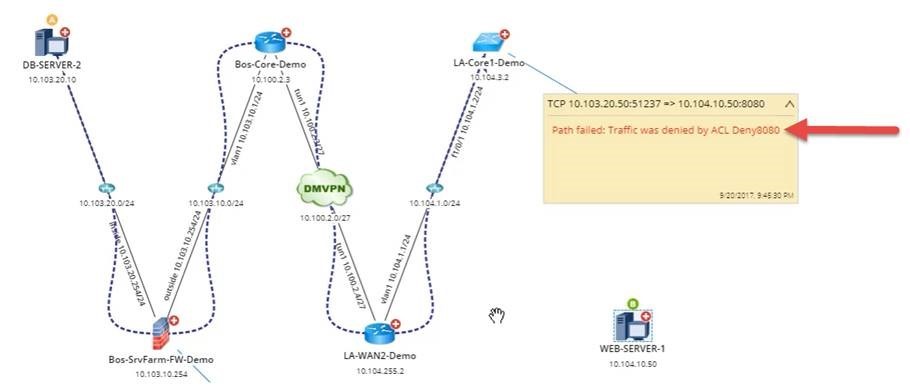
This is where automation becomes useful: rather than making changes that can cause an outage, engineers are able to automate the analysis of traffic flows, as well as the visualization and verification of the result. Traffic monitoring will notice the problem only after it has affected the network. Network verification could understand whether or not any given change violates the intended traffic flow, and prevent the engineer from causing an outage.
Organizations can map outbound traffic flows with NetBrain’s A/B path calculator, allowing for careful monitoring of ports and protocols. NetBrain’s A/B calculator analyzes every hop of the path, factoring advanced technologies like policy-based routing, NAT, access lists, and much more. With policy-based routing, it becomes that much more useful to have a visual presentation of application paths, as well as automated compliance checks during troubleshooting.
Fixing network problems is like curing an illness. While network monitoring tools can easily detect symptoms, they don’t proactively help prevent the underlying causes. Network verification can help network engineers avoid the ailment in the first place. And you don’t get ambushed by those Monday morning fire drills.