The Era of Proactive Network Operations
For decades, network teams have been fighting fires with limited visibility. We can see devices, interfaces, and links, but we’ve been missing the most critical piece: understanding what the network...
New ACE+ Partner Program – Now with Cloud Hosting Option at Unlimited Scale
by NetBrain Nov 7, 2023
Network security is a critical exercise in continuous vigilance. Threats evolve, and new vulnerabilities are discovered every day. Case in point, on October 16th, 2023, Cisco revealed the existence of previously unknown vulnerabilities, CVE-2023-20198 and CVE-2023-20273 (Cisco Bug ID: CSCwh87343). This exploit affects Cisco’s IOS XE products by taking advantage of IOS XE’s web-UI functionality. It works regardless of whether the functionality is configured for HTTPS or not. Per the Cisco website:
These vulnerabilities allow a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
This bug received a Common Vulnerability Scoring System (CVSS) score of 10. This rating is reserved for the most severe vulnerabilities, which warrant immediate action to resolve.
NetBrain’s no-code Network Intents are the fastest way to respond to any real-world network problem. Every network engineer can apply this instant automation without programming or coding.
Our customer support engineers sprang into action within minutes of receiving the Cisco security advisory. They began plugging these security vulnerabilities using our no-code network automation. We knew time was of the essence and wanted to assist our customers in responding quickly within their own hybrid networks.
On that first day, we supplied materials to all our customers. NetBrain power users could use them to create Network Intents to identify CVE-affected IOS XE devices. This network-wide identification allowed their operators to repair each affected device.
Let’s discuss how NetBrain’s Next-Gen platform helped customers identify where they were vulnerable and open to attack.
Cisco’s CVE advisory recommended disabling both the HTTP and HTTPS servers. Respectively, you’d use the “no ip http server” and “no ip http secure-server” commands. If your devices do have HTTP and HTTPS servers enabled, these log messages are some of the most reliable indicators of a compromised system.
%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line %SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023 %WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename
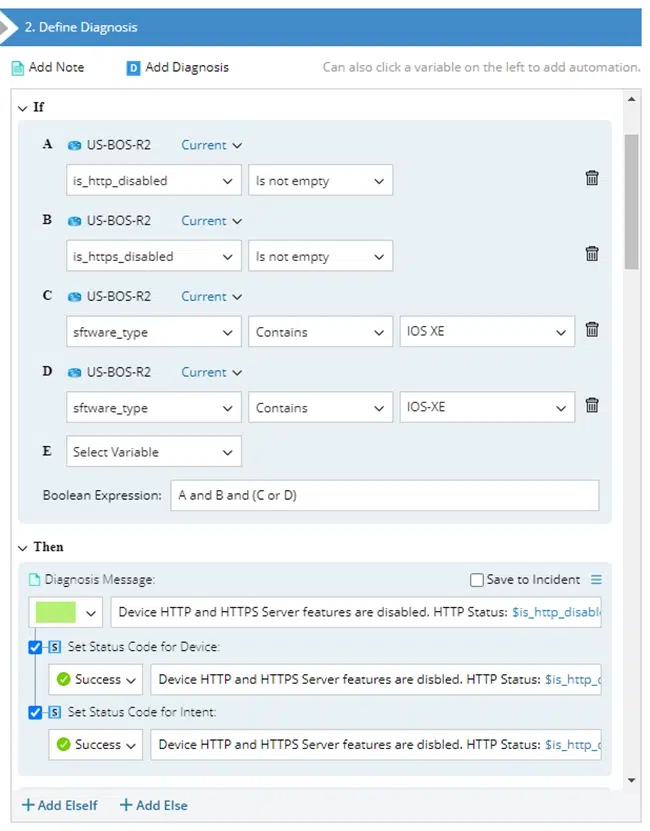
Given the set of indicators provided by Cisco, NetBrain’s no-code interface lets us create automation mimicking what an SME would do, but at scale. For these vulnerabilities, we built a pair of Network-Intent-based assessments:
Our interactive network automation Intents promptly empowered clients to detect and mitigate vulnerabilities.
If you look beyond this CVE problem at the bigger opportunity, you’ll find many aspects need constant assessment, including:
Other aspects include known root causes of common service desk tickets, security policies, and access control architecture.
Make continuous network assessment easy. Use NetBrain Next-Gen and its Network Intent and Preventive Automation technologies. The platform can automatically and continuously test for any condition or operating parameter — at scale!
NetBrain recommends continuously scheduling Intents like the ones designed for this CVE. This approach helps prevent these vulnerabilities from reappearing in the future. Next-Gen’s core capabilities in our Preventive Automation module include continuous network assessment. With our no-code network automation and automated vulnerability assessment, you can continuously validate a broad set of operating conditions. Make automated, continuous network assessment the cornerstone of your service delivery and outage prevention strategy.
No-code network automation scales your NetOps capacity in minutes, not months. As operational threats continue to evolve, maintaining a proactive approach to network vulnerability management is crucial. Responding to countless service incident reports daily is ineffective and costly.
We designed NetBrain Next-Gen with that singular goal in mind. Leverage your network experts’ knowledge to effectively scale their experience through no-code.
Our four-layer Digital Twin becomes the foundation for no-code automation. It provides real-time details about:
Although the Cisco bug example is extreme, you can repeat the same simple no-code approach for any operating condition. No-code automation is ideal if you need to verify or maintain an operating condition. The steps to create an automation from scratch, without any software developers or programming, are:
Network operations are an ongoing process, and no-code network automation should be the foundation for that process. Your real-time business can’t devote time and resources to addressing latent, hidden issues. Your network engineers must act and play to their strengths as soon as new threats emerge. In doing so, protect your business, network, and reputation from potential harm.
For decades, network teams have been fighting fires with limited visibility. We can see devices, interfaces, and links, but we’ve been missing the most critical piece: understanding what the network...
At 2 AM on a Tuesday, a primary data center link fails. By the time the monitoring alerts wake an on-call engineer, customer transactions have been failing for 12 minutes....
From Reactive to Proactive: How we believe NetBrain Turns Gartner’s Outage Prevention Strategies into Reality If you’re a head of IT operations, few things keep you up at night like...
We use cookies to personalize content and understand your use of the website in order to improve user experience. By using our website you consent to all cookies in accordance with our privacy policy.