AI + AUTOMATION
Network Security Automation
Protect your network security investments so they can protect your business. NetBrain doesn’t just monitor your network—it interrogates it. Every configuration, every rule, and every design get scrutinized, validated, and enforced—applying Zero Trust principles and cybersecurity adaptive segmentation to eliminate blind spots.


01
Enforce Security to Reduce Risk
- Automated Network & Cloud Discovery & Visibility
Automatically discover and inventory all network and cloud assets in real time. Detect unauthorized devices and maintain compliance with up-to-date topology maps—aligned with Zero Trust “never trust, always verify” policies. - Zone Security Configuration Validation
Automate security policy checks across firewalls, cloud groups & networks. Enforce Cybersecurity mesh architecture (CSMA) micro-segmentation to prevent lateral movement and block exposure risks. - Vulnerability Detection & CVE Validation
Continuously detect known vulnerabilities (CVEs) across your hybrid environment—with Zero Trust context—so you can patch threats and reduce exposure. - Network & Cloud Observability for Threat Detection
Continuously analyze traffic to detect anomalies and unauthorized access—using cybersecurity-aware analytics to enable rapid response across hybrid environments. - Multi-Layer Security Assessment
Ensure comprehensive protection across network security rules, cloud/SDN policies, compliance, and applications—with built-in Zero Trust posture checks.


02
Visualize a More Secure Network
True network security starts with complete, real-time visibility—and NetBrain delivers exactly that. By automating discovery, mapping, and integration, we empower you to see, secure, and optimize your entire infrastructure—with Zero Trust enforcement at every layer.

Automated Asset Discovery
No more blind spots. NetBrain instantly inventories all devices, topologies, and configurations across hybrid environments, giving you a single source of truth for your network.
Dynamic Mapping & Pathing
Forget static diagrams that expire the moment they’re created. NetBrain generates live, on-demand maps—complete with real-time path analysis—so you always know exactly how traffic flows.
Accurate Documentation
Get a comprehensive inventory data of your network, including device data, module data, interface data, site data and full audit trail.


03
Intent-Based Network Security
An adaptive system comprised of intent-based security that auto-discovers hybrid networks and their network security features, effortlessly creates automation to validate security policies and rules, enforces Zero-Trust principles, and ensures compliance across your multi-vendor infrastructure. No-code automation leverages security intents to assess, monitor, and enforce:
Access Control
Enforce strict access controls by role, department, and vendor permissions:
- Only authenticated HR team members can access HR systems.
- Payroll systems are accessible only by verified finance employees.
- Vendors receive minimal system access, only during predefined business hours.
Zone Segmentation
Adopt a Zero Trust approach to network segmentation: Enforce rules including no zone-to-zone traffic without policy approval, no unfiltered IoT internet access, and complete guest network isolation.
- Workloads in different trust zones must not communicate unless explicitly allowed.
- No direct internet access for IoT devices.
- Isolate guest WiFi traffic from internal systems.
Threat Prevention
Stop threats at every entry and exit point—enforce intents that block malicious IPs, malware uploads, and unauthorized outbound traffic to shrink your attack surface. Enforce rules and policies that:
- Lock-down of known malicious IPs network-wide
- Block file uploads matching malware signatures
- Deny all outbound traffic unless explicitly allowed
Risk Reduction & Compliance Enforcement
Protect sensitive data everywhere—isolate it from public exposure, enforce encryption, and guarantee compliance with GDPR, HIPAA, and leading frameworks (NIST, CIS).
- Isolate sensitive data from public internet exposure
- Enforce encryption for all data—at rest and in transit
- Automate GDPR, HIPAA, and internal compliance policies
- Continuously assess against NIST, CIS, and CVE standards

04
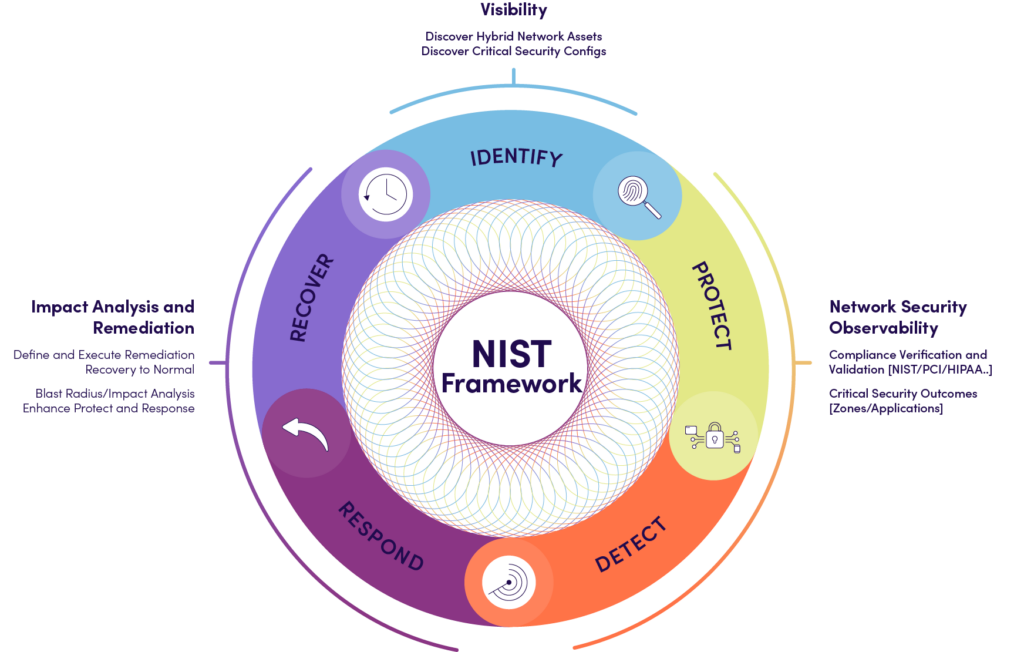
3-Angle NIST Framework Approach
- Visibility
Auto-discover and dynamically map and path hybrid network assets and their critical security configurations as well as traffic flows. - Observability
Utilizing the power of continuous assessment, automation proactively validates compliance mandates and regulations, including NIST, PCI-DSS, HIPAA, and others, without requiring human intervention to achieve the desired security outcomes. - Impact Analysis & Remediation
For every response, there should be a recovery plan. NetBrain’s Dynamic Mapping, Triggered Automation Framework, AI Insight, and Auto-Remediation triage any security incident to aid in rapid diagnosis and remediation.



05
Network Security Observability
Continuously validate critical configurations like AAA, ACLs, and TACACS and states against your golden configs and intents to eliminate vulnerabilities before they arise.
- Proactively assess for NIST/PCI/custom security intent deviations
- Alert instantly on violations or configuration drift
- Visualize easily with summary device/zone/application dashboards
Device Security
Ingest and understand the latest CVE and NIST vulnerabilities and track EOL/EOS to lock down network security.
Application Security
Understand how traffic flows across zones and if any path deviates from its golden application path. Everything you need to auto-remediate any drift is within one click.
Zone Security
Enforce what traffic is allowed or disallowed between DMZ and production zones for every tier of all critical applications.


06
Cloud Network Security
From network layers to applications, in-depth security assessments that expose vulnerabilities and keep your cloud environment airtight. Powerful API integrations provide real-time insights into risks, empowering you to act before threats emerge.

Defense-in-Depth
Automates checks across 4 critical security layers:
- Network: Encryption, DDoS protection, firewall deployment.
- Server: VM security (e.g., public IP exposure, SSH compliance).
- Data: Storage account permissions, encryption settings.
- Application: Path-based security (e.g., firewall deny rates, abnormal traffic spikes).
Multi-layered Security Observability
Native cloud topology visibility helps verify VPN gateway health or flag risks by detecting misconfigured security groups blocking critical traffic or unencrypted VNets.
No-code API integration
With cloud-native tools (e.g., AWS CloudWatch, Azure Monitor) for real-time metrics. Supports multi-layer security checks (network, server, data, application tiers). Pulls data from AWS Security Hub or Azure Monitor to centralize alerts (e.g., IAM risks, DDoS events).
Pre-Built Cloud Automation Library
Ready-to-use automation assessment dashboard templates for cloud security and compliance checks (AWS/Azure/GCP) aggregates cloud-native alerts for faster triage.


