Automation for Network Leaders
As a network operations manager or leader, you are responsible for the changes that drive success. One critical change to consider is switching from manual network management to automated management....
Join us at NetBrain LIVE 2025!
by Valerie DiMartino Jul 17, 2025
Don’t you wish everything in life was as simple as an app store – “there’s an app for that” was the slogan everyone knew. The absolute simplicity of browsing an app store, instantly downloading a solution for nearly any need. Imagine bringing that same level of effortless problem-solving to the complex world of network and security operations. For too long, network automation has meant custom scripting, lengthy development cycles, and the constant re-invention of the wheel for common challenges.
But what if there was a curated marketplace for network automation – a place where pre-built, ready-to-use solutions were just a click away?
Welcome to the era of the Golden Assessment Library (GAL), truly the “App Store for Network Automation,” transforming how organizations achieve network piece of mind in today’s dynamic, hybrid environments.
The era of manual network management is rapidly drawing to a close. In today’s complex, hybrid environments, relying solely on human intervention for network reliability and security is not just inefficient, it’s a critical vulnerability. This is where the concept of a Golden Assessment Library (GAL) emerges not just as a tool, but as a strategic imperative, truly acting as the “App Store for Network Automation”, transforming network operations from reactive firefighting to proactive, intent-driven defense.
Network and security operations teams are constantly battling misconfigurations, policy drift, and the overwhelming task of validating network health across diverse, multi-vendor infrastructures. Traditional methods struggle to keep pace with dynamic changes, leaving organizations exposed to outages and security breaches. The sheer volume of checks, from BGP stability to ACL audits and NIST compliance, consumes valuable time and resources, often leading to human error.
The Golden Assessment Library (GAL) fundamentally redefines how network reliability and security are enforced. It’s a pre-built library of ready-to-use automated assessments.
Comprised of industry-wide outage knowledge, the Golden Assessment Library (GAL) adds a protective layer of assurance to your network, enabling “herd immunity” by learning from past incidents and applying automated validation to detect misconfigurations before they cause outages.
The strategic imperative is clear: embrace the Golden Assessment Library to not just manage, but truly master your network’s reliability and security in the face of ever-evolving needs and threats.
Available to every NetBrain customer, GAL’s power lies in its dual-component approach:
1. Golden Intent Library: This component assesses network health (e.g., BGP neighbor stability, OSPF routing, device performance) and proactively detects risks such as misconfigurations and security gaps. It provides curated, automated checks to validate against best practices and standards, enabling an intent-based approach to network management. For example, it supports comprehensive assessments across various systems, topologies (L2, L3, MPLS, VxLAN, IPSec VPN), routing protocols (EIGRP, OSPF, ISIS, BGP, Static Route), multicast, performance, redundancy (HSRP, VRRP, HA), and device security. It extends to public cloud environments like AWS, GCP, Azure, and SDN/SD-WAN platforms such as Cisco ACI, Cisco SD-WAN, and VMware VeloCloud SD-WAN.
2. Golden Config Library (Plugin-Discovered): This part identifies devices with similar configurations, groups them, and sets the most frequent configuration as the “golden” standard. This is crucial for identifying deviations and manually configured errors – for instance, detecting when one device in a group of ten has a differing NTP server configuration. This library supports extensive configuration auditing for various ACL types (Cisco IOS, Nexus, IOS XR, Arista) and prefix lists across multiple vendors and routing protocols.
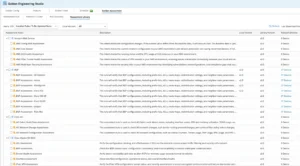
In the context of the Golden Assessment Library (GAL), Relevance is a critical metric that indicates precisely how many devices within your network environment match the criteria of a specific assessment. This concept ensures that your automated checks are always applied to the right devices, providing accurate and actionable insights.
Relevance is determined by how devices align with three key criteria:
The system meticulously analyzes device relevance to ensure precision in your assessments:
1. Based on the Assessment Feature: The system first determines relevance by counting the number of devices that match the broad criteria of the Assessment Feature. This gives you an initial overview of how many devices are potentially subject to a given assessment.
2. Based on the Assessment Rule:
![]()
By precisely calculating relevance, the Golden Assessment Library eliminates guesswork, ensuring that your automated network reliability and security checks are always accurate, targeted, and highly effective. This precision is fundamental to truly proactive network management.
The true value of a Golden Assessment Library extends beyond mere automation; it empowers network ops teams to adopt a proactive, automated, and outcome-driven approach to network operations.
As a network operations manager or leader, you are responsible for the changes that drive success. One critical change to consider is switching from manual network management to automated management....
In today’s complex network environments, managing and resolving repetitive incidents efficiently is paramount. Manual troubleshooting and sifting through countless support tickets can be a major drain on resources, leading to...
The Digital Operational Resilience Act (DORA) entered into application across the European Union on 17 January 2025, reshaping how financial institutions manage cyber and operational risk [1]. Although the United...
We use cookies to personalize content and understand your use of the website in order to improve user experience. By using our website you consent to all cookies in accordance with our privacy policy.