What is VTP in Networking?
VTP is a Cisco Layer 2 protocol that maintains VLAN consistency across a switched network. It distributes VLAN configuration data, like VLAN IDs and names, throughout a VTP domain so you don’t need to configure VLANs on every switch manually. VTP operates by sending advertisements across trunk links. Each advertisement carries VLAN details along with a configuration revision number.
When a switch in the same VTP domain receives an advertisement, it compares the revision number to its local database. If the received revision number is higher, the database is overwritten. This mechanism ensures all switches in the domain share the same VLAN configuration.
The three main modes are:
- Server mode: This mode allows creation, modification, and deletion of VLANs and distributes updates across the domain.
- Client mode: Changes aren’t possible in this mode, but it applies updates received from a VTP server.
- Transparent mode: It forwards advertisements but maintains its own local VLAN database.
The advantage of VTP is centralized management, but it also introduces risk. If a switch with a higher revision number and incorrect VLAN data joins the domain, it can overwrite the correct VLAN database across all devices, causing widespread outages — a VTP bomb.
A Firsthand Account of VTP Gone Wrong
Early in my career, I laughed along with engineers making jokes about the dreaded VTP bomb, but I always thought the disaster stories were more of an exaggeration than reality. Surely VTP hadn’t destroyed networks as much as they suggested? Something about the simplicity of the VTP seems to make it dangerous in the hands of a careless engineer. And, unfortunately, I’ve been that careless engineer.
The Project and Our Initial Approach
In the days when the ink on my CCNA certification was still wet, I worked on a switch refresh project for a large school district. The customer gave us several parameters such as default gateways, DNS servers, SNMP community strings, hostnames, and — you guessed it — VTP information. Still, we never did a discovery of their network. We didn’t have the hours to dig into their infrastructure, so instead of finding out which VTP server was and its revision number, we slapped configs on switches and planned our cutovers.
The deployment progressed quickly as we spent evenings swapping out closet switches, and I enjoyed it very much. The school was quiet, and we had massive amounts of pizza and coffee to keep us going. At the end of the hall, we had a small stereo playing our favorite classic rock station.
When Things Went Wrong
While we debated who was the best grunge band of all time, a security guard stopped by to tell us the bus garage was offline. He had no access to the security cameras, email, or the internet. He wasn’t very concerned, so neither were we.
However, when we saw all the APs blinking and wall-phones unregistered, we knew we had a problem. We were working on only one closet, which had its share of connections for APs and phones, but it looked like the entire building was down. In fact, the bus garage was a separate building altogether, so we knew something was seriously hosed.
Configuring VTP requires only a handful of commands, but manually investigating every switch, one by one, is error-prone and time-consuming.
Thankfully, figuring out the issue didn’t take long. We logged into the core switch and poked around. It didn’t take a room full of CCIEs to see no VLANs on the switch. After more investigation, we noticed there were none on the entire network, other than VLAN 1, of course.
The Dreaded VTP Bomb
Someone plugged in a switch with a higher VTP revision number than everything else and wiped the entire network’s VLAN configuration. We didn’t know which switch was the culprit or which one of us did it, but I’m pretty sure it was me because my co-worker was focused on cabling.
VTP bombs may not be quite as serious an issue anymore with the advent of VTP version 3, which introduced safeguards against this. However, the real solution to VTP incidents is a thorough understanding of the network and proper configuration of new devices.
Configuring VTP requires only a few commands, and getting a good grasp of how VTP is operating on a network likewise requires only a handful of commands. The problem is that the access layer has many devices, making a thorough investigation tedious and easy for an engineer to dismiss.
- Show VTP status displays information such as VTP version, revision number, correct VTP domain name, and the operating mode.
- Show VTP devices queries the VTP domain and displays discovered VTP servers and clients.
- The output from the show VTP counters command will show an engineer the VTP activity on a particular device.
In a network of even modest size, this would require going from switch to switch until an engineer was sure they covered every device. At best, doing this manually is error-prone and tedious. At worst, engineers avoid doing it altogether.
How We Handled It
My co-worker and I were able to get the VLANs back onto the core switch and repair some of the damage, but we still needed to go switch by switch to find the stragglers and paste VLANs into them. We got an earful for our carelessness, but we ultimately got everything up and running, though it took hours of manual configuration.
Because I experienced my own VTP-related incident, I don’t laugh much anymore when someone makes a VTP joke. Unfortunately, I was the cause of it, but it wasn’t because I didn’t understand VTP or didn’t know the commands. I didn’t do my due diligence.
What we needed was the power of Dynamic Maps and Runbooks. Discovering a network is tedious and time-consuming, but neglecting it can lead to huge problems. Automation software that mitigates human error and abstracts away the pain not only makes our jobs easier but it safeguards against outages such as the dreaded VTP bomb.
VTP Configuration Best Practices
VTP can clearly bring efficiency to VLAN management, but it also introduces risks that could disrupt entire domains. Engineering teams need clear practices that secure configurations, prevent mismatches, and streamline workflows.
Eliminate VTP Risks Through Automated Network Discovery
NetBrain takes the pain out of network discovery — or any manual configuration on many devices. Built specifically to automate these tasks, Runbook technology provides a framework to gather all the relevant VTP information from a network with only a few clicks. In the screenshot below is a Dynamic Map of a discovered network on the right and a Runbook on the left used to automate gathering VTP information across the entire infrastructure.
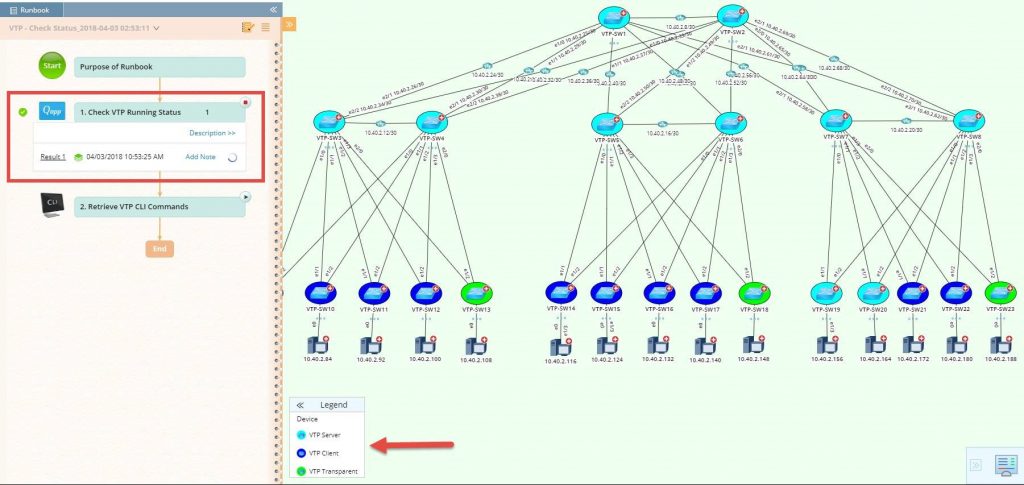 The Dynamic Map highlights VTP roles, VTP server, VTP client, VTP transparent; and VTP domain name, VTP mode, VTP running version, configuration version, and VTP pruning mode are embedded as device-level data tables.
The Dynamic Map highlights VTP roles, VTP server, VTP client, VTP transparent; and VTP domain name, VTP mode, VTP running version, configuration version, and VTP pruning mode are embedded as device-level data tables.
Address Password Mismatch VTP Issues
A password mismatch is a common VTP-related issue and incredibly tedious to check one device at a time. It’s also extremely prone to human error. Because a Runbook works from a Dynamic Map of discovered devices and has within it all the commands an engineer would run, NetBrain is able to automate an entire troubleshooting workflow — completing tasks in seconds rather than hours.
In the screenshot below, notice that the Runbook specifically runs Qapps — actions to find common VTP configuration problems such as password mismatches.
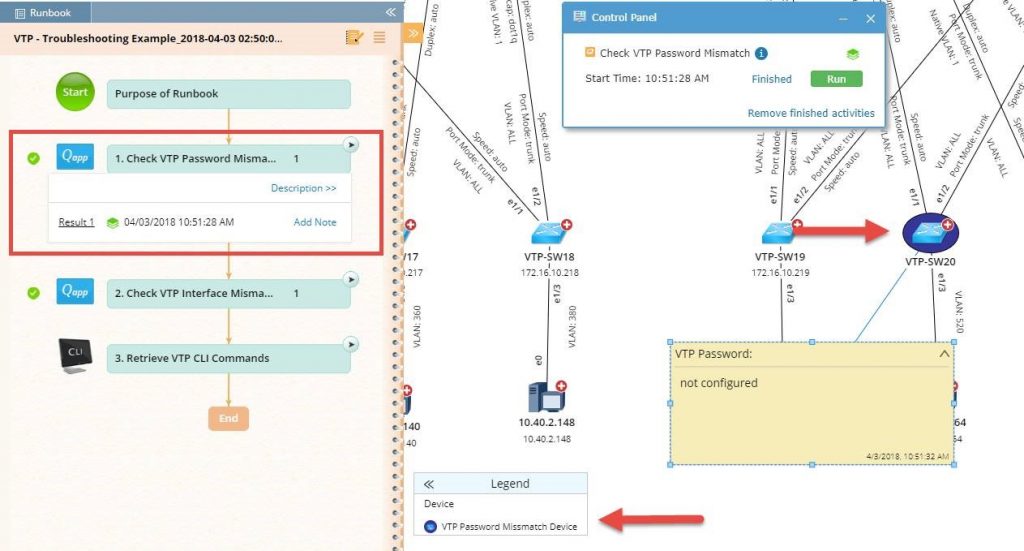 Runbooks perform all the steps you would — only automatically instead of manually command by command, device by device. Here, it checks for password mismatches and highlights the results right on the Dynamic Map.
Runbooks perform all the steps you would — only automatically instead of manually command by command, device by device. Here, it checks for password mismatches and highlights the results right on the Dynamic Map.
Enhance Workflow With NetBrain
The true power of Dynamic Maps and Runbooks is in how they enhance an entire workflow. In the next screenshot, you can see that after checking for VTP password mismatches, the Runbook moves right into the next action to check VTP interface mismatches. In this way, the Dynamic Map and Runbook work together to create a completely automated environment for an engineer instead of having to use console connections and out-of-date spreadsheets.
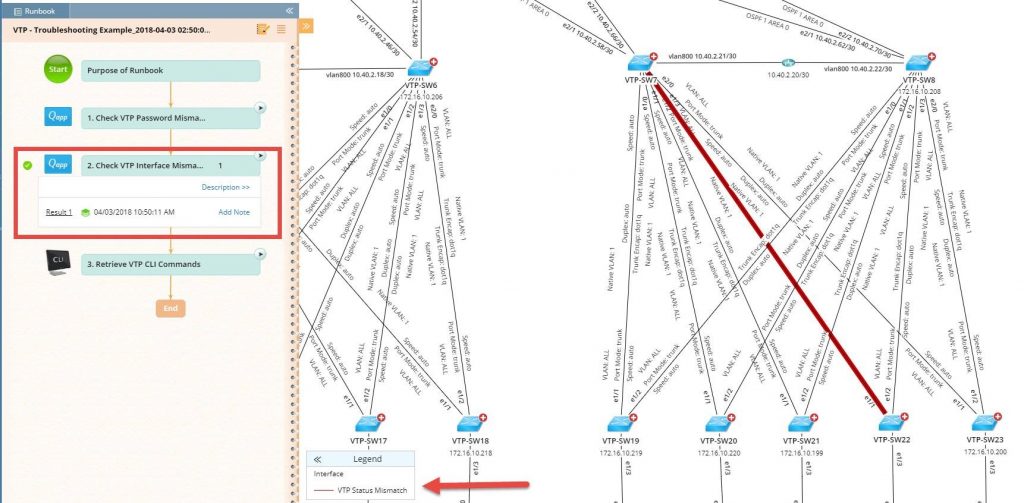 Then the Runbook automatically runs another Qapp to check for interface mismatches — again, across all devices in one fell swoop.
Then the Runbook automatically runs another Qapp to check for interface mismatches — again, across all devices in one fell swoop.
Build Resilient Networks With Automation
Manual VTP management in large-scale networks creates instability and increases risk. NetBrain’s Dynamic Maps and Runbooks remove error-prone tasks by automating configuration checks and monitoring, enabling proactive Cisco VTP troubleshooting and preventing misconfigurations from spreading.
It also speeds up root-cause analysis and gives engineers the visibility and control to operate reliably. As networks grow, this approach protects critical services and enforces the consistency required to scale. See how NetBrain can automate your operations by requesting a demo today.
 The Dynamic Map highlights VTP roles, VTP server, VTP client, VTP transparent; and VTP domain name, VTP mode, VTP running version, configuration version, and VTP pruning mode are embedded as device-level data tables.
The Dynamic Map highlights VTP roles, VTP server, VTP client, VTP transparent; and VTP domain name, VTP mode, VTP running version, configuration version, and VTP pruning mode are embedded as device-level data tables. Runbooks perform all the steps you would — only automatically instead of manually command by command, device by device. Here, it checks for password mismatches and highlights the results right on the Dynamic Map.
Runbooks perform all the steps you would — only automatically instead of manually command by command, device by device. Here, it checks for password mismatches and highlights the results right on the Dynamic Map. Then the Runbook automatically runs another Qapp to check for interface mismatches — again, across all devices in one fell swoop.
Then the Runbook automatically runs another Qapp to check for interface mismatches — again, across all devices in one fell swoop.