From Scripts to Agents: How Evolution of Automation Made AI Inevitable in NetOps
by Brian Soetaert Jan 20, 2026
Broadband, Wi-Fi, and early smartphones pushed enterprise network traffic past the breaking point by 2004. MPLS VPNs suddenly spanned more sites than any engineer could mentally map. Outages crossed multiple domains, and tribal knowledge couldn’t keep up.
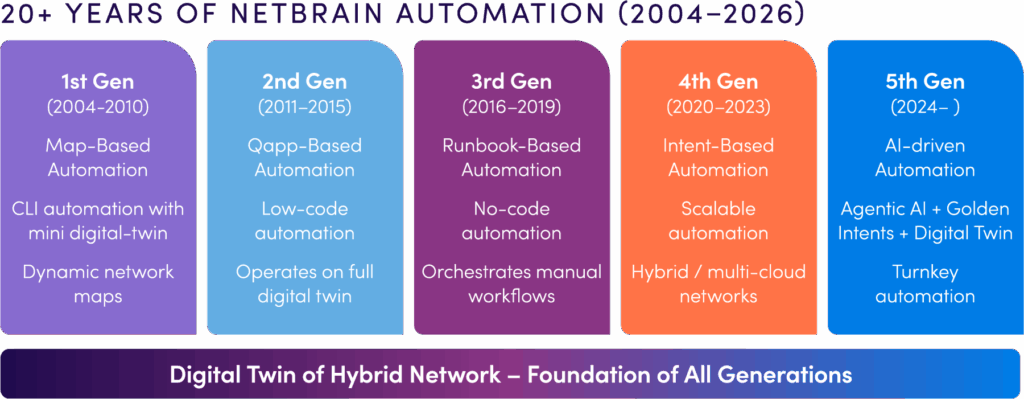
Twenty years later, AI agents troubleshoot networks at machine speed… but only because each generation of automation before them solved a specific limitation. NetBrain’s evolution tracks that path: from visualizing topology, to encoding expertise, to validating intent, to agents that understand goals.
Let’s look at each generation that has led up to the inevitable evolution of AI becoming a critical part of modern NetOps, and how network teams can prepare for the era of agentic AI.
1st Generation: When Visibility Became the Bottleneck (Map-Based Automation, 2004–2010)
Day-to-day operations in the early 2000s meant logging into devices one by one and assembling context mentally. That worked until networks began to span hundreds of devices across multiple locations. When something broke, engineers reconstructed topology from memory, outdated Visio diagrams, and fragmented documentation.
Map-based automation solved the context problem. NetBrain’s first platform combined CLI automation with dynamic topology discovery: a living diagram backed by a digital twin. Engineers could visualize paths, pull device configurations, and see dependencies in real time, instead of hunting through static documents.
Automation gained spatial awareness. Commands came with an immediate understanding of where a device fits in the larger fabric. Just as importantly, network knowledge moved from individual engineers’ heads into a shared, queryable system, centralizing context rather than scattering it across scripts and spreadsheets.
2nd Generation: From Maps to Reusable Logic (Qapp-Based Automation, 2011–2015)
Virtualization changed the rules. Topology could shift without anyone touching physical hardware. The network an engineer saw on Monday might be different by Wednesday, not because of a redesign, but because workloads moved. Maps solved the “where is everything?” problem, but troubleshooting still depended on individual experts running their own command sequences, documented in personal notebooks or one-off scripts.
Incidents crossed virtual switches, firewalls, and early cloud gateways. The same patterns repeated (VPN misconfigurations, QoS issues, asymmetric routing), but the diagnostic procedures remained tribal knowledge.
NetBrain’s second generation introduced low-code Qapps: shareable diagnostic modules that ran against the digital twin. Engineers assembled checks and data pulls using building blocks instead of writing custom scripts for every scenario. The Qapp adapted those checks to whatever topology the digital twin discovered at runtime.
Automation moved from “show me the layout” to “show me what to check and in what order.” When a senior engineer encoded a proven troubleshooting sequence into a Qapp, the entire team could use it. Expertise became software.
3rd Generation: From Diagnostics to Complete Workflows (Runbook-Based Automation, 2016–2019)
By the mid-2010s, the network had been fragmented. Multi-cloud architectures meant application traffic could traverse AWS, Azure, on-prem data centers, and branch offices in a single transaction. Kubernetes and microservices introduced connectivity patterns that shifted constantly. SD-WAN reshaped how branches connected to cloud resources.
Qapps handled discrete diagnostics well, but incidents increasingly required coordination across teams like security validating policies, cloud engineers checking connectivity, and network teams tracing paths. Each group used different tools and followed different procedures. Restoring service meant manually stitching together multiple steps under time pressure.
Runbook-based automation orchestrated entire workflows instead of isolated tasks. A runbook could pull configs, run path analysis, check intent compliance, and document findings in a repeatable sequence. Because runbooks operated on the digital twin, they automatically adapted to the actual topology.
Runbooks encoded the exact sequence a senior engineer would follow during an outage, making that process accessible to anyone. The bottleneck was no longer individual expertise.
4th Generation: When Every Scenario Became Impossible to Script (Intent-Based Automation, 2020–2023)
Pandemic-driven remote work forced organizations to rewire connectivity almost overnight, leaning heavily on VPN, SD-WAN, and cloud gateways. SASE and Zero Trust architectures layered security policy directly into the connectivity fabric. Observability platforms started streaming everything they could capture, flooding teams with telemetry.
With rolling cloud deployments, dynamic security policies, and constantly shifting traffic patterns, pre-scripting every workflow for every failure mode became impossible. Even with well-designed runbooks, the space of possible scenarios was too large. Teams needed to know whether the network still matched what the business expected, not just how to respond when something broke.
Intent-based automation flipped the model. Engineers defined desired outcomes (reachability requirements, segmentation rules, performance thresholds, compliance policies) and let the system validate whether those intents held true across the live network. NetBrain’s fourth generation built on its digital twin to encode these intents and automatically check them against real-time topology and state.
Engineers focused on defining policies and success criteria rather than enumerating every specific check. Automation became continuous verification rather than reactive troubleshooting. This created the foundation AI needed: a system that already understood what “correct” looked like, ready for agents that could reason how to restore it.
5th Generation: From Automation to Autonomous Reasoning (2024– )
Intent-based automation clarified what “good” looks like, but a gap remained. Detecting an intent violation still left engineers manually piecing together logs, paths, policies, and historical changes during high-pressure incidents. The system could flag problems, but humans still had to solve them.
Large language models became practical for enterprise use around 2023. These models could read tickets, parse CLI output, correlate events, and propose hypotheses far faster than humans, provided they had a rich data model to work against. A mature digital twin, codified intents, and AI reasoning capable of operating at machine speed could finally work together.
NetBrain’s fifth generation adds an agentic layer on top of its digital twin and Golden Intents. AI agents can ingest a goal (“restore access for this application without violating security policies”), explore the current state of the network, and choose or assemble the necessary diagnostic and remediation steps within predefined boundaries.
Routine troubleshooting and verification tasks increasingly run at machine speed. Agents escalate only when they hit ambiguity, conflicting intents, or policy boundaries. Engineers design those boundaries, define new intents, and refine the knowledge agents rely on. The role becomes authoring how operations should behave rather than executing them manually.
How NetOps Can Prepare for Agentic AI
Networks now span multiple clouds, remote sites, and security domains. Manual troubleshooting and ad-hoc scripts can’t keep pace. Every unresolved ticket queue and every recurring incident pattern signal that the current generation of automation has hit its ceiling. Engineers spend time reconstructing paths, correlating logs, and re-running familiar checks, which is work machines can handle reliably.
Gartner® predicts “By 2030, AI agents will be the most common approach for executing network runtime activities, up from minimal adoption in late 2025.”
For over a decade, the GUI dashboard has been the primary interface—a window into switches, firewalls, and cloud connections. But according to industry research from Gartner®, that window is closing.
A major shift is underway, one that will redefine not just the tools network teams use, but how the teams operate and where to focus their expertise.
The shift to agentic AI doesn’t eliminate network engineering roles… it redefines them. Engineers become strategic orchestrators rather than daily operators. The expertise remains critical. Now, it’s directed toward defining policies, designing boundaries for AI systems, and handling the exceptions agents can’t resolve. Augmenting human capability, not replacing it.
NetBrain’s trajectory offers a practical migration path. The same architectural choices that made map-based and runbook-based automation effective (dynamic mapping, codified troubleshooting logic, a rich network data model) provide the foundation for AI agents that understand goals and act within guardrails. Organizations can modernize in stages, knowing each step prepares the environment for AI-driven operations.
For teams ready to explore how to pilot agentic capabilities safely and prepare culturally for this shift, get Gartner’s deeper guide to prepare NetOps for agentic AI.
GARTNER is a trademark of Gartner, Inc. and/or its affiliates.
Gartner, The Future of NetOps Is Agentic, By Andrew Lerner, Mike Leibovitz, John Watts, Jonathan Forest, 5 January 2026
Related
The Operating Model to Cut Network Downtime Every Year
Data is not the problem. What you do with it is. For years, network teams have lacked insight into downtime even with… More telemetry. More dashboards. More alerts. … And...
Top Five Use Cases of Agentic NetOps in 2026 and Beyond
Network teams are under pressure from all sides. They must keep complex hybrid networks available and secure, but lack true end‑to‑end visibility, so outages, performance issues, and security gaps can...
The Future of NetOps
NetOps shapes how organizations expand, innovate, and protect their digital ecosystems. Informed by DevOps, NetOps combines hybrid architectures, distributed workloads, and artificial intelligence (AI) powered data centers into fast, adaptable,...
We use cookies to personalize content and understand your use of the website in order to improve user experience. By using our website you consent to all cookies in accordance with our privacy policy.