Configuring LDAP Authentication
Note: Make sure the uid attribute is properly configured on the LDAP server for target group members. The attribute will be used as the login username of the system.
1.Log in to the System Management page.
2.In the System Management page, click User Accounts > External Authentication.
3.Click Add LDAP Authentication. A Wizard is opened to guide you through the steps to connect to the LDAP server and configure the tenant or domain access privileges for the imported user accounts.
1)Enter a unique name to identify the LDAP server and a brief description.
2)Enter the credentials to connect to the LDAP server. See LDAP Server Settings for more details.
3)Click Show Group to find available user groups from the LDAP server. All matched groups are listed in the Groups pane.
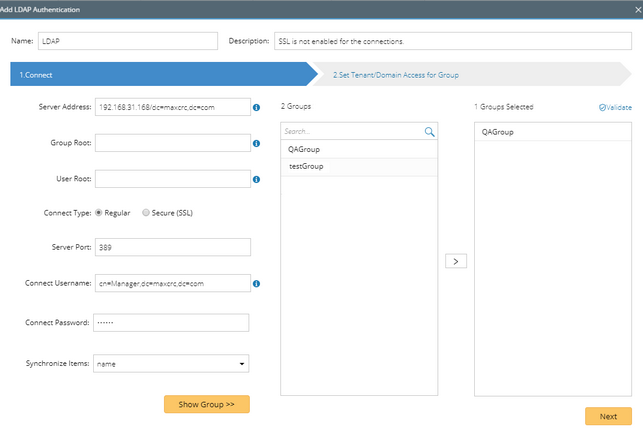
4)Select one or more user groups to import, and then click Next.
Tip: Click Validate to verify whether the selected groups still exist on the LDAP server. Click the 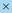 icon to remove an invalid group from the list.
icon to remove an invalid group from the list.
5)Assign domain access and more privileges to the user accounts in the selected groups one by one.
▪System Admin — click to assign the system administrator role to the user accounts. For the detailed privileges of System Management and User Management, refer to Featured Management Privileges.
▪Tenant Access — select one or more tenants to assign access permissions to the user accounts.
▪Tenant Admin — select one or more tenants to assign the tenant administrator role to the user accounts.
▪Allowed to Create Domain — select the check box to assign the domain creation permission to the user accounts.
▪Domain Access — select one or more domains to assign access permissions to the user accounts.
▪Domain Privileges — click Assign Privileges to assign more domain privileges to the user accounts by role. See Share Policy for more details.
6)Click Save.
7)In the pop-up dialog, enter the username and password of a user account under the specified server address or user root and click Verify to authenticate the connection.
8)Click OK in the pop-up dialog.
4.Navigate to the Users tab and click Synchronize With LDAP/AD Server to immediately load the user accounts imported from the LDAP server. Alternately, the user accounts can also be automatically synchronized after the first-time login.
Note: The synchronization only carries out on the enabled authentications. If you add a new user account to the selected group on the LDAP server after the synchronization, the user can immediately log in to the specified domains with the assigned roles and privileges. If you delete any user accounts from the LDAP server, the changes will not be synchronized with the system automatically. You have to manually remove them from the system.
Note: To prevent the assigned roles and privileges of an external user account from being synced with any changed authentication settings, you can lock the user rights as follows. See Creating User Account for more details.
LDAP/AD Server Settings
The following table lists the credentials that are required when connecting to an LDAP/AD server.
Field |
Description |
|---|---|
Server Address |
The hostname or IP address of the LDAP/AD server as well as the search base. Note: The hierarchy of the search base must be higher or contain the hierarchy of the OUs (Organization Unit) which the target user groups or user accounts belong to. Note: If you want to connect to the LDAP/AD server by using its hostname, make sure the firewall on the machine is turned off. |
Group Root |
The OU that the target user groups are located in. For example, ou=G1. |
User Root |
The OU that the target user accounts are located in. For example, ou=U1. Note: If special characters are contained in the Server Address, Group Root, and User Root fields, they must be entered as escaped characters. See escaped characters for more details. |
Connect Type |
The security settings of the connections between the LDAP/AD server and NetBrain Web API Server, Regular or Secure(SSL). To enable SSL connections between the AD server and NetBrain Web API Server, see Using SSL on AD Server for more details. |
Server Port |
The port number used to listen for LDAP/AD requests and send responses. Tip: If the domain users/groups cannot be synchronized successfully, please try: Regular 3268 or SSL 3269. |
Connect Username |
The username to connect to the server. Note: It is highly recommended to use the domain name/username format in the Connect Username field to avoid unexpected problems. For example, test/administrator. Note: When more than 500 user groups are managed on the LDAP server, the username used to connect to the server must be the Manager. An example of the connect username: CN=Manager,dc=test,dc=com. |
Connect Password |
The password of the user to connect to the server. Click change password if you want to modify it. To restore the last password, click use last password. |
Synchronize Items |
The select items to synchronize from LDAP/AD server to the system. By default, the Username item is selected. |
See also:
