Configuring TACACS+ Authentication
1.Log in to the System Management page.
2.In the System Management page, click User Accounts > External Authentication.
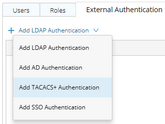
3.Click the ![]() icon and select Add TACACS+ Authentication from the drop-down list.
icon and select Add TACACS+ Authentication from the drop-down list.
|
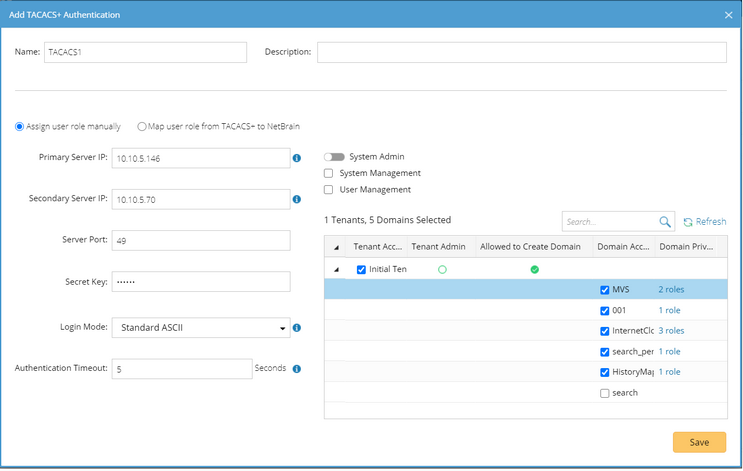
1)Enter a unique name to identify the TACACS+ server and a brief description. 2)Keep the Assign user manually option selected. 3)Enter the required credentials and parameters to connect to the TACACS+ server. See TACACS+ Server Settings for more details. 4)Assign the system roles and privileges to all the user accounts on the TACACS+ server. ▪System Admin — click to assign the system administrator role to the user accounts. For the detailed privileges of System Management and User Management, refer to Featured Management Privileges. ▪Tenant Access — select one or more tenants to assign access permissions to the user accounts. ▪Tenant Admin — select one or more tenants to assign the tenant administrator role to the user accounts. ▪Allowed to Create Domain — select the check box to assign the domain creation permission to the user accounts. ▪Domain Access — select one or more domains to assign access permissions to the user accounts. ▪Domain Privileges — click Assign Privileges to assign more domain privileges to the user accounts by role. See Share Policy for more details. 5)Click Save. |
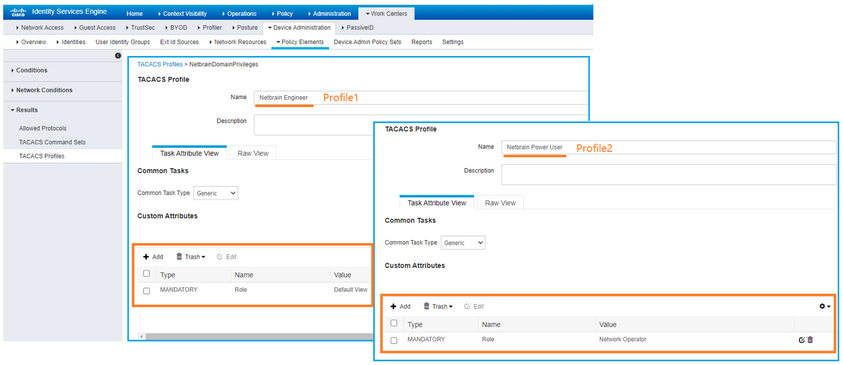
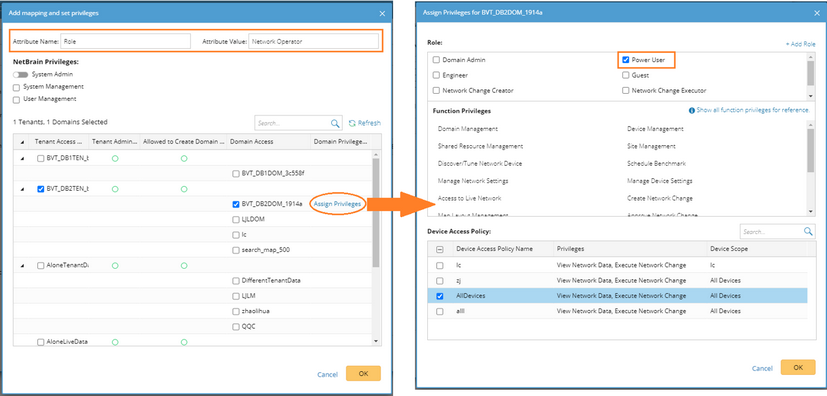
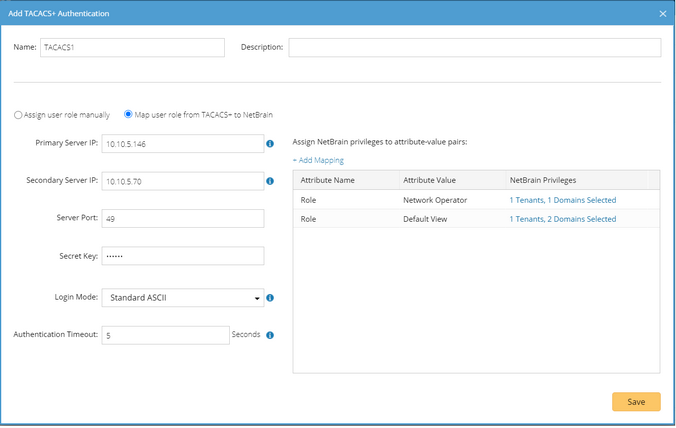
For example, you have two TACACS profiles with two different roles defined in your ISE system, and you want to map them respectively to the IE system roles “Power User” and “Engineer”. 1)Enter a unique name to identify the TACACS+ server and a brief description. 2)Select the Map user role from TACACS+ to NetBrain option. Note: This option only applies to Cisco ISE and Cisco ACS 5.x. 3)Enter the credentials and parameters to connect to the TACACS+ server. See TACACS+ Server Settings for more details. 4)Click Add Mapping to add a new attribute/value pair (Role/Network Operator), assign the Power User role to it and click OK. ▪System Admin — click to assign the system administrator role to the user accounts. For the detailed privileges of System Management and User Management, refer to Featured Management Privileges. ▪Tenant Access — select one or more tenants to assign access permissions to the user accounts. ▪Tenant Admin — select one or more tenants to assign the tenant administrator role to the user accounts. ▪Allowed to Create Domain — select the check box to assign the domain creation permission to the user accounts. ▪Domain Access — select one or more domains to assign access permissions to the user accounts. ▪Domain Privileges — click Assign Privileges to assign more domain privileges to the user accounts by role. See Share Policy for more details. 5)Click Add Mapping to add a new attribute/value pair (Role/Default View), assign the Engineer role to it, and click OK. 6)Click Save. |
4.In the pop-up dialog, enter the username and password of any existing user accounts on the TACACS+ server and click Verify to authenticate the connection.
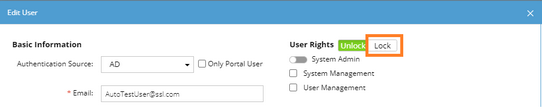
Note: To prevent the assigned roles and privileges of an external user account from being synced with any changed authentication settings, you can lock the user rights as follows as soon as the user has logged in to the IE system. See Creating User Account for more details.
TACACS+ Server Settings
The following table lists the credentials that are required when connecting to a TACACS+ server.
Field |
Description |
|---|---|
Primary Server IP |
The IP address of the primary TACACS+ server. |
Secondary Server IP |
The IP address of a backup TACACS+ server. It is used when the primary TACACS+ server is unavailable. If you do not have the backup server, leave this field empty. |
Server Port |
The port number used to listen for TACACS+ authentication requests and send responses. Make sure it is consistent with the port number you have configured on the TACACS+ server. |
Secret Key |
The password used to access the TACACS+ server. Make sure it is consistent with the key that you have configured on the TACACS+ server. |
Login Mode |
The authentication method used to encrypt the connections to the TACACS+ server. Four types of login modes are supported: Standard ASCII, PAP, CHAP, and MS-CHAP. Make sure it is consistent with the authentication method you have configured on the TACACS+ server. |
Authentication Timeout |
The time interval between sending authentication password and getting an authentication response from the TACACS+ server. When the authentication time exceeds the threshold, it will be treated as an authentication timeout and an error message will be displayed. |