R12 Publication-2025July16
Creating AWS Access Policy and Role for Monitored Accounts
- Go to Policies in Identity and Access Management (IAM).
- Create a new resource access policy to grant read access to the services for monitoring purposes.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"autoscaling:Describe*",
"autoscaling-plans:Describe*",
"autoscaling-plans:GetScalingPlanResourceForecastData",
"cloudwatch:Describe*",
"cloudwatch:Get*",
"cloudwatch:List*",
"directconnect:Describe*",
"ec2:Describe*",
"ec2:Get*",
"ec2:SearchTransitGatewayRoutes",
"network-firewall:DescribeFirewall",
"network-firewall:DescribeFirewallPolicy",
"network-firewall:DescribeRuleGroup",
"network-firewall:ListFirewallPolicies",
"network-firewall:ListFirewalls",
"network-firewall:ListRuleGroups",
"network-firewall:ListTagsForResource",
"elasticloadbalancing:Describe*"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
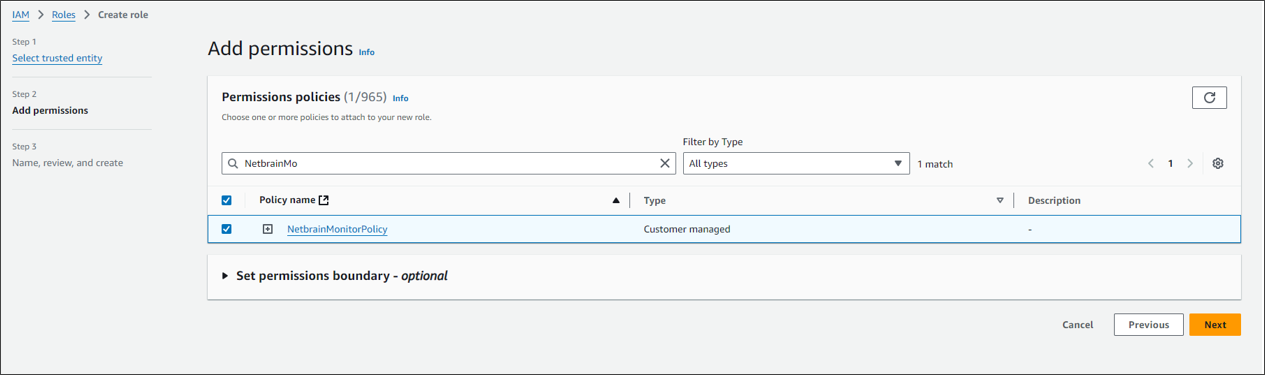
Once the policy is created, you need to attach this policy to the role.
Follow the steps below to configure the role:
- Go to Roles in Identity and Access Management (IAM).
- Create a new role by selecting Trusted entity type as Custom trust Policy. Add a Trust policy to allow the EC2 instance’s Role from the gateway account to assume this role.
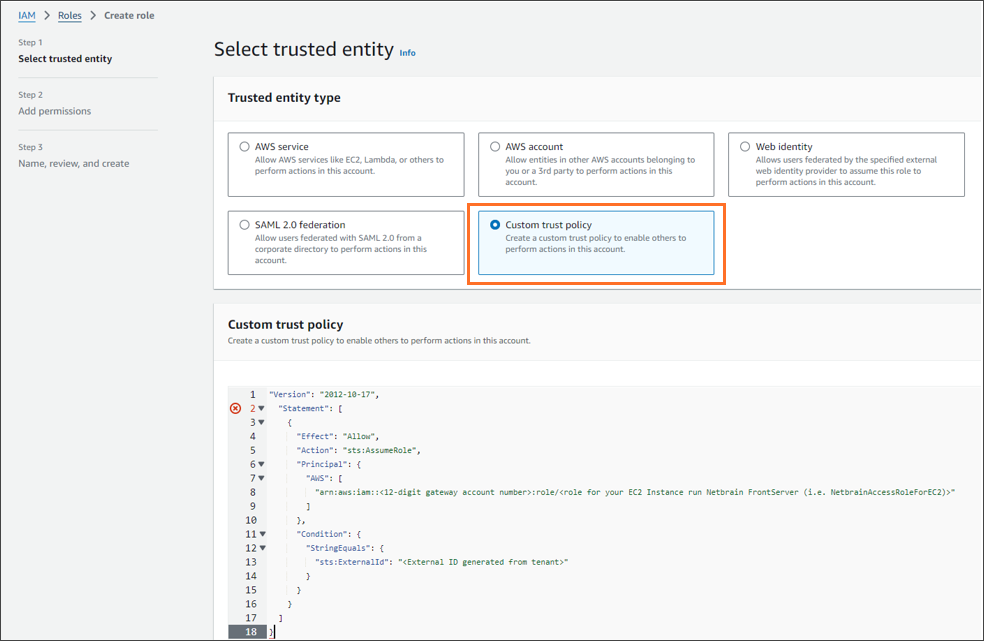
The following is a sample of trust relationship JSON statements. Replace the placeholders for Account ID, Role Name, and External ID with the values specific to your configuration.
Note: The EC2 instance role name, such as NetbrainAccessRoleForEC2, must match the role name configured in the gateway account. Code"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Principal": {
"AWS": [
"arn:aws:iam::<12-digit gateway account number>:role/<role for your EC2 Instance run Netbrain FrontServer (i.e. NetbrainAccessRoleForEC2)>"
]
},
"Condition": {
"StringEquals": {
"sts:ExternalId": "<External ID generated from tenant>"
}
}
}
]
} - Attach the policy (created previously) to the role.