R12 Publication-2025July16
Configuring EC2 Role for NetBrain Front Server in AWS Gateway Account
This section illustrates how to create a role for an EC2 instance in the gateway account using the AWS console. This will allow the EC2 instance that hosts NetBrain system to access the monitored accounts.
- Go to Roles in Identity and Access Management (IAM) and create a new role.
-
Select AWS service and EC2 for this role.

-
Enter the role name (NetbrainAccessRoleForEC2).

Note: The role name shall match the one you previously picked when configuring the trusted relation in the monitored account.
Skip the Permissions (policy) section in the wizards. The policy will be added later.
-
After the role is successfully created, open the role and attach an inline policy to allow the EC2 instance to assume NetbrainAccessRole in monitored accounts.
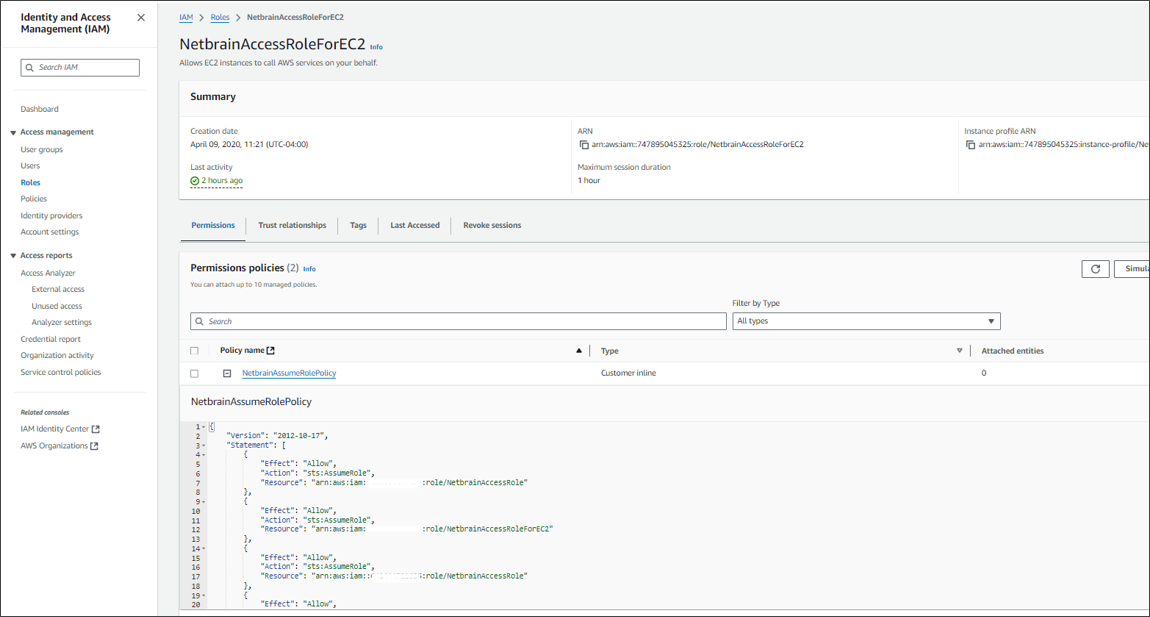
A sample policy JSON is as follows.

Note: Use the account ID to monitor your environment.
Code"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<12-digit first monitored account number>:role/<role created in previous step (NetbrainAccessRole)>"
},
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": ""arn:aws:iam::<12-digit second monitored account number>:role/<role created in previous step (NetbrainAccessRole)>""
}
]
}
- To discover the resources of an AWS Gateway account in NetBrain, you must add a new resource access policy to the associated role. This policy grants read access to the required AWS services for resource discovery.
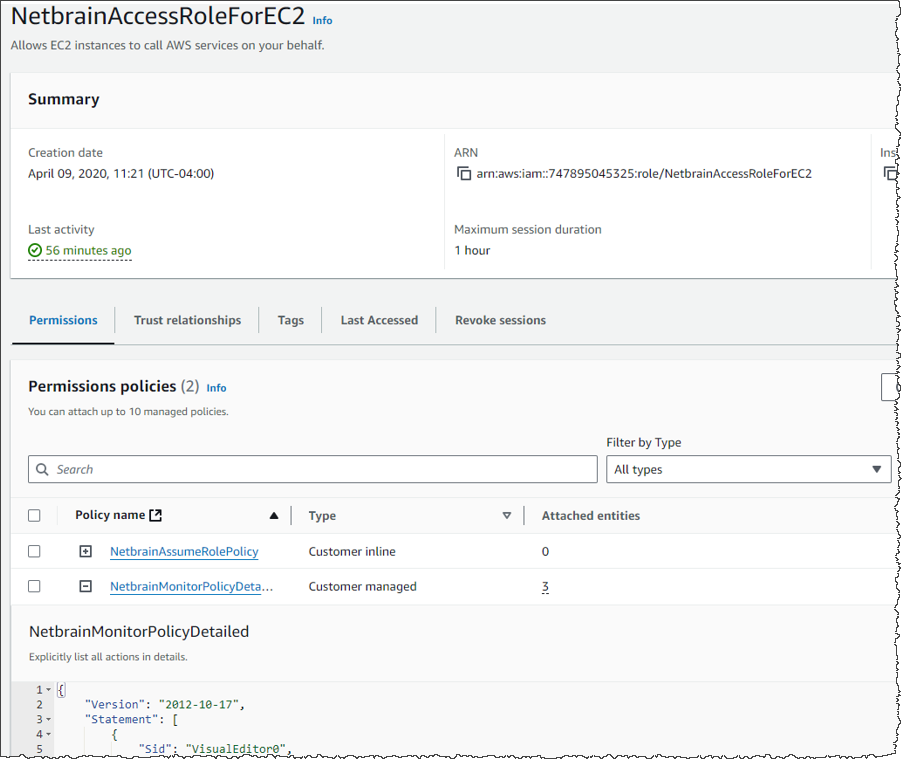 Code
Code{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"autoscaling:Describe*",
"autoscaling-plans:Describe*",
"autoscaling-plans:GetScalingPlanResourceForecastData",
"cloudwatch:Describe*",
"cloudwatch:Get*",
"cloudwatch:List*",
"directconnect:Describe*",
"ec2:Describe*",
"ec2:Get*",
"ec2:SearchTransitGatewayRoutes",
"network-firewall:DescribeFirewall",
"network-firewall:DescribeFirewallPolicy",
"network-firewall:DescribeRuleGroup",
"network-firewall:ListFirewallPolicies",
"network-firewall:ListFirewalls",
"network-firewall:ListRuleGroups",
"network-firewall:ListTagsForResource",
"elasticloadbalancing:Describe*"
],
"Effect": "Allow",
"Resource": "*"
}
]
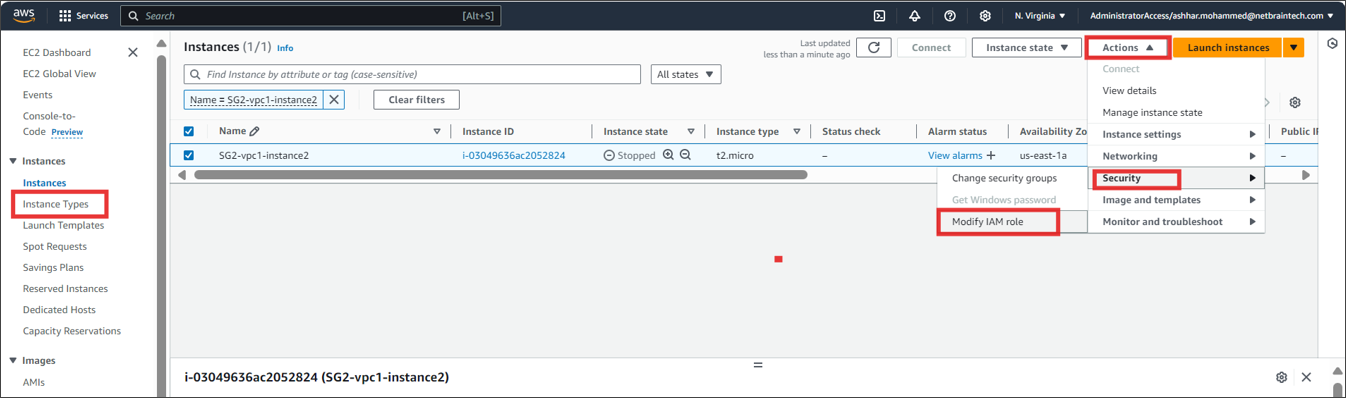
} Find the EC2 instance where you run NetBrain Front Server, and attach the role to it. You can also specify the role when first launching an EC2 instance.