Assign IAM Permissions
There are different approaches to assign your IAM permissions to the service principal created before based on various scenarios and needs. Recommended best practices are shown below,
Best Practices 1:
Scenario: Discover resources of all the Projects under the Organization.
Permissions assignment approach: Assign all the required permissions (or system roles) under the Organization.
Organization Roles Required:
- Browser (ID: roles/browser)
- Compute Organization Security Policy User (ID: roles/compute.orgSecurityPolicyUser)
- Compute Viewer (ID: roles/compute.viewer)
- DNS Reader (ID: roles/dns.reader)
- Logs Viewer (ID: roles/logging.viewer)
- Monitoring Viewer (ID: roles/monitoring.viewer)
- Private Logs Viewer (ID: roles/logging.privateLogViewer)
- Service Usage Viewer (ID: roles/serviceusage.serviceUsageViewer)
Best Practices 2:
Scenario: Discover resources of some Projects under the Organization.
Permissions assignment approach: Assign the Organization required permission or system roles under Organization level. And assign the Project required permission or system roles under Project level.
Organization Role Required:
- Browser (ID: roles/browser)
- Compute Organization Security Policy User (ID: roles/compute.orgSecurityPolicyUser)
- Logs Viewer (ID: roles/logging.viewer)
- Monitoring View (ID: roles/monitoring.viewer)
- Private Logs Viewer (ID: roles/logging.privateLogViewer)
- Service Usage Viewer (ID: roles/serviceusage.serviceUsageViewer)
Projects Role Required:
- Compute Viewer (ID: roles/compute.viewer)
- DNS Reader (ID: roles/dns.reader)
The principal of these best practices is to ensure the resources discovered by NetBrain should be assigned with IAM permission in the organization-scope or project-scope properly.
Required build-in Role for Org:
- Browser (ID: roles/browser)
- Compute Organization Security Policy User (ID: roles/compute.orgSecurityPolicyUser)
- Logs Viewer (ID: roles/logging.viewer)
- Monitoring Viewer (ID: roles/monitoring.viewer)
- Private Logs Viewer (ID: roles/logging.privateLogViewer)
- Service Usage Viewer (ID: roles/serviceusage.serviceUsageViewer)
Required built-in roles for Projects:
- Compute Viewer (ID: roles/compute.viewer)
- DNS Reader (ID: roles/dns.reader)
- Logs Viewer (ID: roles/logging.viewer)
- Monitoring Viewer (ID: roles/monitoring.viewer)
- Private Logs Viewer (ID: roles/logging.privateLogViewer)
- Service Usage Viewer (ID: roles/serviceusage.serviceUsageViewer)
- Go to IAM & Admin > IAM, select the GCP Organization or Project from the top drop-down menu, and then click GRANT ACCESS.
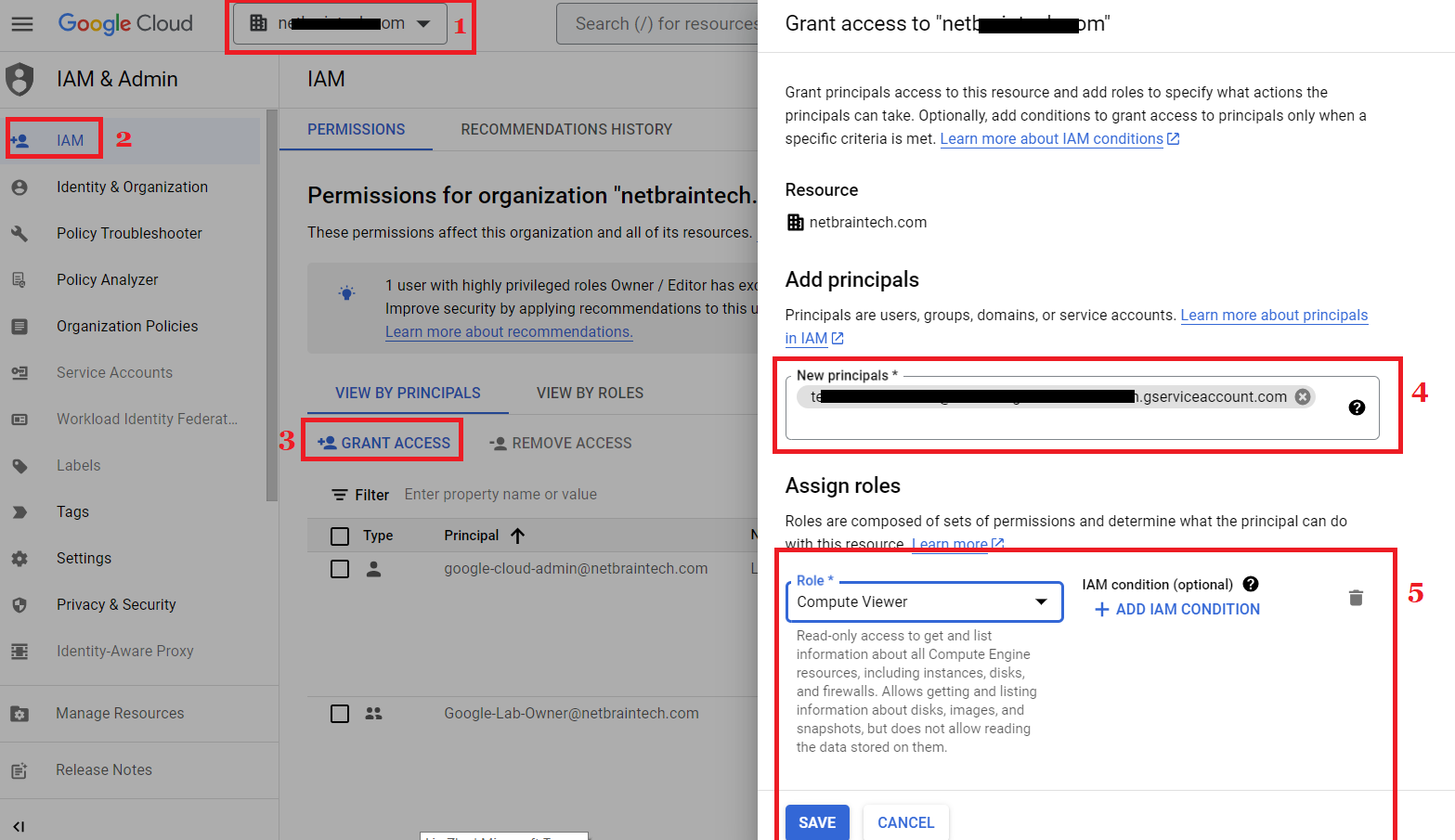
- Paste the service account email under the New principals, select the system role required in the Role field, and click SAVE.
