10.1.15.12-06212024
Creating AWS Access Policy and Role for Monitored Accounts
- Go to Policies in Identity and Access Management (IAM).
- Create a new resource access policy to grant read access to the services for monitoring purposes.
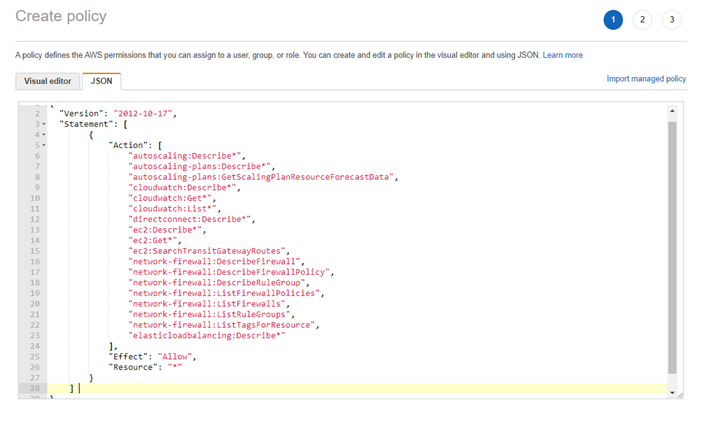
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"autoscaling:Describe*",
"autoscaling-plans:Describe*",
"autoscaling-plans:GetScalingPlanResourceForecastData",
"cloudwatch:Describe*",
"cloudwatch:Get*",
"cloudwatch:List*",
"directconnect:Describe*",
"ec2:Describe*",
"ec2:Get*",
"ec2:SearchTransitGatewayRoutes",
"network-firewall:DescribeFirewall",
"network-firewall:DescribeFirewallPolicy",
"network-firewall:DescribeRuleGroup",
"network-firewall:ListFirewallPolicies",
"network-firewall:ListFirewalls",
"network-firewall:ListRuleGroups",
"network-firewall:ListTagsForResource",
"elasticloadbalancing:Describe*"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
Follow the steps below to configure the role:
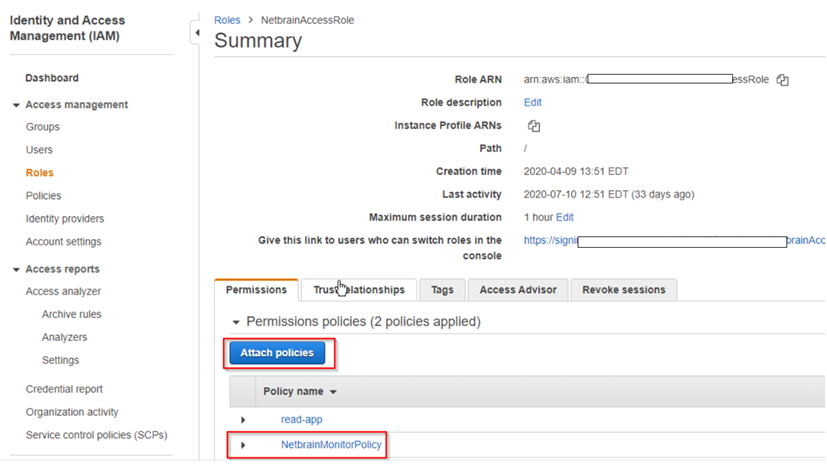
- Go to Roles in Identity and Access Management (IAM).
- Create a new role.
- Attach the policy (created previously) to the role.
- Go to Trust relationships and add the statements to allow the EC2 instance from the gateway account to assume this role.

Note: The role name of the EC2 instance, for example, NetbrainAccessRoleForEC2, must match the EC2 instance role name configured in the gateway account. 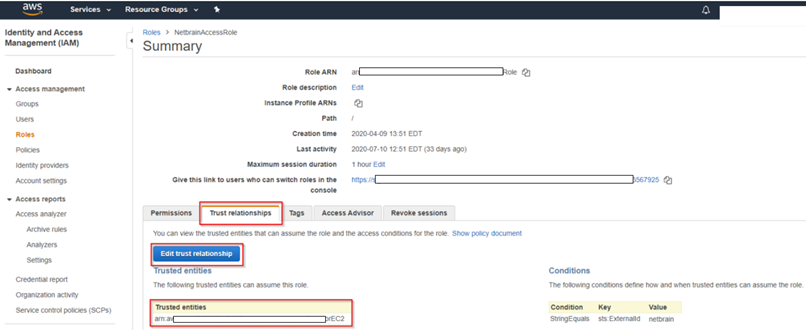
The sample trust relationship JSON statements are as follows. You need to replace the account ID, role name, and External ID to reflect your specific configuration.Code"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Principal": {
"AWS": [
"arn:aws:iam::<12-digit gateway account number>:role/<role for your EC2 Instance run Netbrain FrontServer (i.e. NetbrainAccessRoleForEC2)>"
]
},
"Condition": {
"StringEquals": {
"sts:ExternalId": "<External ID generated from tenant>"
}
}
}
]
}