10.1.15.12-06212024
Audit Logs For Device Access
The system provides the capability to capture logins and executed commands on devices. The relevant data is recorded in audit log for device access.
- Log in to System Management Page.
- Go to Home Page > Audit Logs for Device Access to review logs related to device interactions and activities.
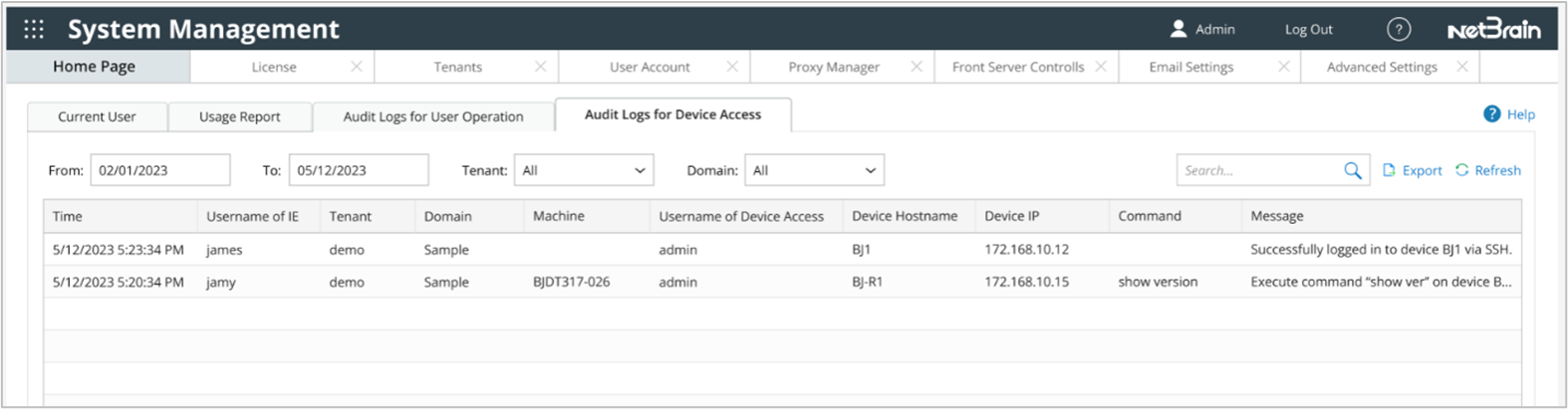
- Filter log: You can filter the log in the following two ways:
- Define the period of log data you want to check: Select the From, To field to specify the time period of the audit log.
- Define the scope of log data you want to check: Select Tenant and Domain to check the log for specific tenant and domain.
- Search the log: Input keywords in the search bar. The 'Search' field supports all columns except Time/Tenant/Domain.
- View the log in the table below. You can view the details of the device access, such as time, username, tenant and domain, the machine, device access username, device IP, command used, and the message (status of login).The message section provides essential details about device actions, including login method, success or failure status, and executed commands. This information is valuable for monitoring and troubleshooting network devices. E.g.,a. Successfully logged in to device BJ*POP via SSH.b. Failed to log in to device BJ*POP via Telnet.c. Execute command "show ver" on device BJ*POP.In the Smart CLI, a uniform message, 'Log in device BJ*POP via SSH,' will be used for all login attempts.
- (Optional) Click Export to export the log. The file will be exported in csv format.