 by Barbara.Froemmel Aug 25, 2017
by Barbara.Froemmel Aug 25, 2017
Ensuring a network is properly secured and meets PCI compliance standards for audits is a growing concern for many organizations. While they may be operating within compliance boundaries, most find it difficult to prove it both internally and for regulatory audits. This is due in large part to the fact that documentation of existing network infrastructure is routinely manual and often out-of-date.
For many, the absence of an automated solution has led to a limited view and understanding of security policies along credit card transaction flows. Further complicating matters is the fact that network and security teams don’t often collaborate and seldom see eye-to-eye.
With these factors in mind, we have outlined three critical phases to ensuring success during a PCI compliance audit.
Validation through documentation
Documentation is the most critical step for teams to prove compliance. However, the ongoing issue for most companies is the manual and arduous nature of the process. The inability to document firewall policies, access-lists, policy-based routing, and more in the case of an audit is a real problem.
With Dynamic Network Maps, organizations can automate the existing network in detail to not only provide end-to-end visibility, but offer detailed asset reports and more. To validate credit card transaction paths, engineers need a way to assess all possible paths. NetBrain’s A/B path calculator works at the layer-4 port-level to analyze ACLs and policy-based routing to visually present the application paths and allow the automation of PCI compliance checks across the relevant devices.
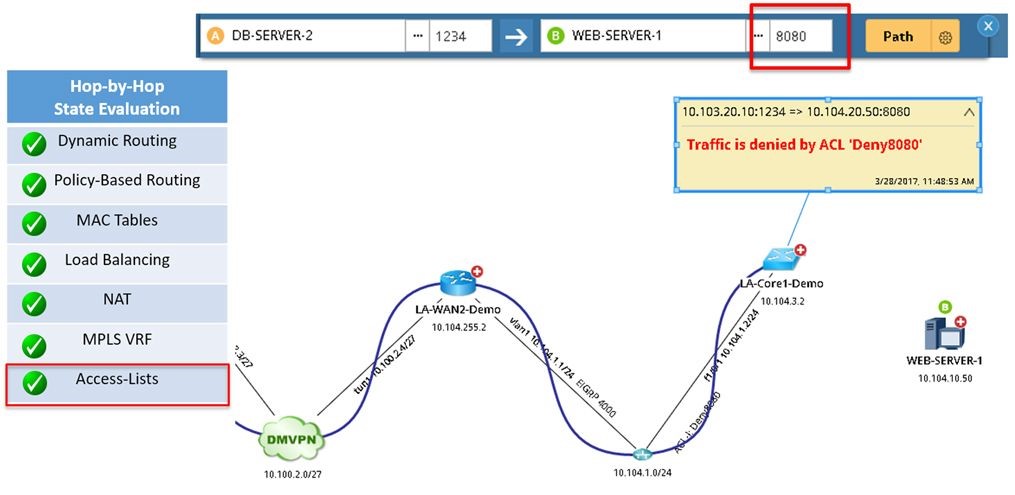
Figure 1: NetBrain’s A/B calculator performs a comprehensive analysis at every hop of the path, factoring advanced technologies like policy-based routing, NAT, access-lists, and much more.
Standardize security processes through Runbooks
Validating every network configuration against a common set of compliance rules (e.g. device passwords are encrypted, timeouts are configured, no vendor defaults are present) is an important step towards PCI compliance. Many organizations run into compliance troubles when making changes to the network. To combat this, security teams can create Executable Runbooks to use for network changes to ensure compliance through new service deployments and operational changes. These Executable Runbooks may include design guides and best practices to help enforce security best practices going forward.
Upon configuring a change, implementation engineers should also execute a vulnerability assessment Runbook to ensure that it meets pre-defined PCI compliance standards. An event management system can even be configured to auto-trigger a PCI assessment at the instant a change takes place.
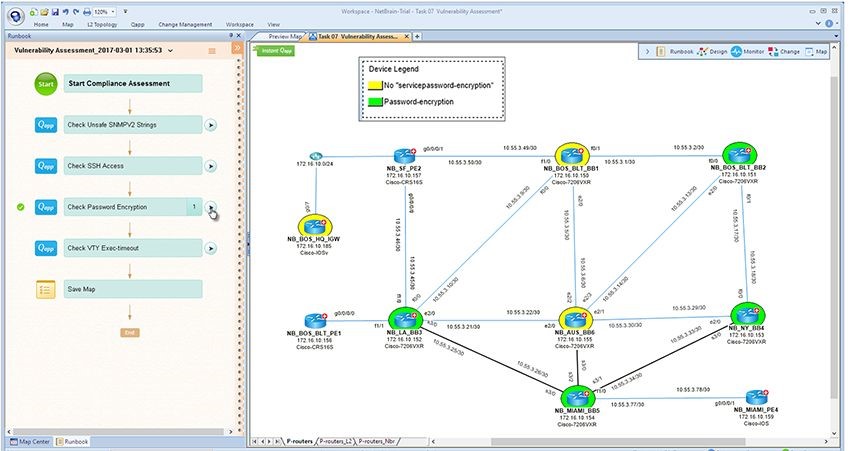
Figure 2: To ensure every network device is access-hardened, this sample runbook checks every config file against a set of security standards. A design engineer executes this once across the entire network and then for every new configuration change.
Compliance isn’t a one-time event
Staying PCI compliant is an ongoing process, not a onetime fix. So is guarding against potential security threats. For the entire process to work effectively, collaboration is imperative. With NetBrain, security teams and network teams can work collaboratively through the platform during triage, forensics, and for security to proactively prevent threats.
Ensuring that proper compliance procedures are adhered to during and after a cyberattack and that network teams follow defined security practices is critical. And remember, it’s not enough to say what you did during an audit, you must prove it.

